The Principle of Least Privilege (PoLP), a cornerstone of robust security, dictates that a system should grant users and processes only the minimum necessary permissions to perform their tasks. In the context of serverless computing, particularly with AWS Lambda functions, this principle takes on paramount importance. Over-permissioned Lambda functions represent a significant attack vector, potentially allowing malicious actors to compromise resources and data.
This exploration will dissect the intricacies of applying PoLP to Lambda functions, providing a structured approach to securing your serverless applications.
We will navigate the complexities of Identity and Access Management (IAM) roles and policies, crucial components in enforcing PoLP within the AWS ecosystem. The discussion will encompass best practices for identifying necessary permissions, structuring IAM policies for maximum security, and employing tools for monitoring and auditing Lambda function access. Furthermore, this analysis will offer practical examples, including an in-depth examination of S3 and database access scenarios, equipping readers with the knowledge to implement PoLP effectively and enhance the security posture of their serverless deployments.
Understanding the Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) is a fundamental security concept. It dictates that a subject (e.g., a user, a process, a Lambda function) should only be granted the minimum necessary access rights (privileges) to perform its intended function. This principle is a cornerstone of robust security practices, significantly reducing the potential impact of security breaches.
Core Concept of the Principle of Least Privilege
PoLP fundamentally restricts access. The goal is to minimize the potential damage if a security compromise occurs. Instead of providing broad, encompassing permissions, PoLP emphasizes granting only the specific permissions required for a subject to complete its tasks. This approach limits the scope of potential damage.
Real-World Examples Illustrating the Impact of PoLP
The effectiveness of PoLP is best understood through concrete examples demonstrating how it mitigates security risks. These examples highlight how limiting access can contain and reduce the impact of various threats.
- Scenario 1: Compromised User Account A user account with excessive privileges is compromised. The attacker, with elevated access, can potentially access sensitive data, modify system configurations, and install malicious software. However, if the user account only had the minimum required permissions, the attacker’s actions would be significantly constrained. For example, if a user only needed read access to a specific database, the attacker would be limited to viewing the data, preventing them from modifying or deleting it.
- Scenario 2: Vulnerability Exploitation in a Software Application Consider a web application with a vulnerability that allows an attacker to execute arbitrary code. If the application runs with elevated privileges, the attacker could potentially gain control of the entire system. Implementing PoLP, however, would restrict the application’s permissions, limiting the attacker’s ability to cause significant damage. For instance, if the application only has access to specific files or directories, the attacker’s ability to access or modify other system resources would be curtailed.
- Scenario 3: Insider Threat A disgruntled employee with broad access to sensitive data poses a significant security risk. They could intentionally leak confidential information or sabotage critical systems. Applying PoLP limits the employee’s access to only the necessary data and resources required for their job. This significantly reduces the potential for data breaches or system disruption caused by malicious insiders. For example, if an employee only needs access to sales data, they would not be able to access financial records or other sensitive information.
Benefits of Implementing PoLP in Any System
Implementing PoLP offers numerous benefits, primarily focusing on reducing the attack surface. By limiting the scope of access, the overall security posture of a system is significantly enhanced.
- Reduced Attack Surface By granting only necessary permissions, PoLP minimizes the potential impact of a security breach. An attacker’s ability to move laterally within a system or escalate privileges is significantly curtailed. The attack surface is the total area of a system that is vulnerable to attack. Reducing this surface decreases the likelihood of successful attacks.
- Improved Security Posture Implementing PoLP makes it more difficult for attackers to gain unauthorized access to sensitive data or resources. This improves the overall security posture of the system, making it more resilient to various types of attacks. A strong security posture protects against a wider range of threats and improves the system’s ability to withstand attacks.
- Simplified Security Auditing Systems implementing PoLP are easier to audit and monitor. With clearly defined permissions, it is simpler to identify and track unauthorized access attempts or potential security vulnerabilities. This simplifies compliance efforts and allows for more efficient security incident response.
- Enhanced Data Protection PoLP contributes to better data protection by restricting access to sensitive information. This reduces the risk of data breaches, unauthorized data modification, and data loss. This protects the confidentiality, integrity, and availability of critical data.
Applying PoLP to Lambda Functions
Implementing the Principle of Least Privilege (PoLP) within serverless architectures, specifically with AWS Lambda functions, presents unique challenges. While the benefits of PoLP are well-established, the dynamic nature and distributed architecture of serverless environments require careful consideration. This section will delve into the specific hurdles encountered when applying PoLP to Lambda functions, comparing the security ramifications of different permissioning approaches and highlighting common pitfalls in implementation.
Challenges of Applying PoLP to Serverless Architectures
The serverless paradigm, characterized by its ephemeral nature and reliance on managed services, complicates the application of PoLP. Several inherent characteristics of Lambda functions introduce difficulties in adhering to the principle.
- Granularity of Permissions: Lambda functions often interact with a multitude of AWS services, each with its own set of permissions. Accurately determining the precise set of permissions required for a function to operate effectively can be a complex and time-consuming process. The sheer number of potential permissions and their interactions increases the likelihood of errors.
- Dynamic Resource Creation: Serverless applications frequently provision resources on demand. A Lambda function might, for example, create an S3 bucket or a DynamoDB table. Determining the necessary permissions
-before* resource creation requires careful planning and potentially the use of infrastructure-as-code tools, which adds complexity. - Function Invocation and Execution Context: Lambda functions can be triggered by various events (e.g., API Gateway requests, S3 object creations, CloudWatch events). The execution context of the function, including the identity it assumes, varies depending on the trigger. This necessitates careful configuration of both the function’s execution role and the permissions of the services that invoke it.
- Debugging and Monitoring: Debugging permission-related issues in a serverless environment can be challenging. Errors related to insufficient permissions may manifest in obscure ways, requiring thorough logging and monitoring to identify the root cause. Analyzing CloudTrail logs and Lambda function logs becomes critical for troubleshooting access problems.
Security Implications of Over-Permissioned vs. Under-Permissioned Lambda Functions
The security posture of a Lambda function is significantly influenced by its assigned permissions. The consequences of both over-permissioning and under-permissioning are substantial.
- Over-Permissioned Lambda Functions: A Lambda function with excessive permissions poses a significant security risk. If compromised, an attacker gains access to a broader attack surface. This can result in:
- Data Breaches: An attacker could access and exfiltrate sensitive data stored in S3 buckets, databases, or other resources that the function has permission to access.
- Resource Manipulation: The attacker could modify or delete resources, such as terminating EC2 instances, modifying database records, or corrupting data.
- Privilege Escalation: An attacker could leverage the function’s permissions to gain further access to other resources or services, potentially compromising the entire AWS account.
- Under-Permissioned Lambda Functions: A Lambda function lacking sufficient permissions will fail to execute its intended tasks. While this may seem less dangerous than over-permissioning, it can lead to:
- Service Disruptions: The application functionality reliant on the Lambda function will be unavailable, impacting users and potentially causing business disruptions.
- Operational Overhead: Developers will spend time troubleshooting and correcting permission errors, delaying releases and increasing operational costs.
- Security Vulnerabilities (Indirectly): Frustration with permission issues might lead to shortcuts or workarounds, such as granting overly broad permissions to expedite development, thereby inadvertently introducing security risks.
Common Mistakes in Assigning Permissions to Lambda Functions
Developers often make mistakes when assigning permissions to Lambda functions, which can compromise security. Understanding these common errors is crucial for improving security practices.
- Using Wildcard Permissions: Granting permissions using wildcards (e.g., `s3:GetObject*` or `dynamodb:*`) is a widespread and dangerous practice. It grants excessive access, allowing the function to perform unintended actions on resources.
- Over-reliance on Managed Policies: While AWS-managed policies can be convenient, they often provide broader access than necessary. Relying solely on these policies can lead to over-permissioning.
- Failing to Regularly Review Permissions: Permissions should be reviewed periodically to ensure they remain appropriate. As applications evolve and new features are added, the required permissions may change. Failing to update permissions accordingly can lead to security vulnerabilities.
- Granting Permissions Based on Service Type, Not Specific Resource: Instead of granting broad permissions to an entire service (e.g., `s3:*`), permissions should be scoped to specific resources (e.g., a particular S3 bucket). This minimizes the impact of a potential compromise.
- Not Utilizing Resource-Based Policies: Resource-based policies, such as those used for S3 buckets or KMS keys, can restrict access to specific resources. Developers often overlook the use of these policies, leading to unnecessary exposure.
- Incorrectly Configuring IAM Roles: The IAM role assigned to a Lambda function defines its identity and the permissions it has. Incorrectly configuring this role, such as assigning an overly permissive policy, can result in security vulnerabilities.
IAM Roles and Policies: The Foundation of Lambda Security
IAM roles and policies are fundamental to securing Lambda functions. They dictate the permissions a Lambda function has, controlling its access to other AWS resources. Properly configured roles and policies are critical for implementing the principle of least privilege, ensuring that functions only have the necessary access and minimizing the potential impact of security breaches. This section details the role of IAM in Lambda security, explores the different policy types, and provides a practical example of a least-privilege policy.
IAM Roles and Lambda Function Security
IAM roles are central to the security of Lambda functions. A role defines a set of permissions that a Lambda function assumes when it executes. This mechanism allows Lambda functions to interact with other AWS services without requiring hardcoded credentials. Instead, the role provides temporary security credentials. These credentials are automatically provided to the Lambda function at runtime.
The role’s permissions determine which actions the function can perform and which resources it can access. This approach simplifies security management, reduces the risk of compromised credentials, and allows for fine-grained control over resource access. The role effectively acts as an identity for the function within the AWS ecosystem.
IAM Policy Types and Their Implications
IAM policies define the specific permissions associated with an IAM role. These policies are written in JSON and specify which actions are allowed or denied on which resources. Understanding the different types of IAM policies is crucial for effective security management.
- Managed Policies: Managed policies are standalone policies created and managed by AWS or by you. AWS managed policies are pre-defined policies created by AWS to cover common use cases, like providing read-only access to S3. Customer managed policies are created by you and can be attached to multiple IAM roles. Using managed policies, both AWS and customer managed, can simplify permission management, but it’s crucial to review the permissions granted by these policies to ensure they align with the principle of least privilege.
For example, the “AmazonS3ReadOnlyAccess” policy grants read-only access to all S3 buckets in an account, which might be broader than what a Lambda function requires.
- Inline Policies: Inline policies are embedded directly within an IAM role. They are specific to that role and cannot be reused. Inline policies provide the most granular control, as they allow for tailored permissions. However, managing many inline policies can become complex and harder to maintain, especially in environments with numerous Lambda functions. Inline policies are suitable when the permissions are very specific to a single role and are unlikely to be shared.
The choice between managed and inline policies depends on the specific use case and the desired level of control. For complex scenarios, a combination of both types might be used. The key is to carefully evaluate the permissions granted by each policy type and to adhere to the principle of least privilege.
Designing a Basic IAM Policy for S3 Access
To illustrate the application of the principle of least privilege, consider a Lambda function that needs to read objects from a specific S3 bucket. The following is a sample IAM policy (in JSON format) designed to grant the function only the necessary permissions:“`json “Version”: “2012-10-17”, “Statement”: [ “Effect”: “Allow”, “Action”: [ “s3:GetObject” ], “Resource”: [ “arn:aws:s3:::your-bucket-name/*” ] ]“`This policy allows the Lambda function to perform only the `s3:GetObject` action (reading objects) on objects within the specified S3 bucket (`your-bucket-name`).
It does not grant permission to list the bucket contents, write objects, or perform any other S3 operations.
- “Version”: “2012-10-17”: Specifies the version of the policy language.
- “Statement”: []: An array of individual statements.
- “Effect”: “Allow”: Specifies that the action is permitted.
- “Action”: [“s3:GetObject”]: Lists the specific S3 action allowed. This is the only action required for the Lambda function to read objects.
- “Resource”: [“arn:aws:s3:::your-bucket-name/*”]: Specifies the S3 bucket and objects to which the action applies. The `*` wildcard indicates that the function can access all objects within the bucket. This follows the principle of least privilege by limiting access to only the required resource.
This policy is an example of applying the principle of least privilege. It grants the Lambda function only the minimum permissions required to perform its task, reducing the potential attack surface and minimizing the impact of any security breaches. The use of a specific bucket and object path further restricts access.
Identifying Necessary Permissions for Lambda Functions
Determining the exact permissions a Lambda function requires is a critical step in implementing the Principle of Least Privilege. Over-permissioning can lead to security vulnerabilities, while under-permissioning can cause function failures. This section Artikels a systematic approach to identify and define the precise permissions necessary for a Lambda function to operate effectively and securely.
Process for Determining Exact Permissions
The process of identifying the required permissions is iterative and involves analyzing both the function’s code and its interaction with AWS resources. It’s essential to adopt a proactive approach to minimize potential security risks.The following steps detail this process:
- Code Analysis: Examine the Lambda function’s code for any calls to AWS services or resources. This includes identifying the specific API calls, the resources they access (e.g., S3 buckets, DynamoDB tables, API Gateway endpoints), and the operations performed (e.g., read, write, delete).
- Resource Identification: For each AWS service accessed, determine the exact resources the function interacts with. For example, if the function reads data from an S3 bucket, identify the specific bucket and the objects within it. Avoid broad permissions like “s3:*” that grant access to all S3 resources.
- Permission Mapping: Based on the API calls and resource interactions, map the necessary AWS permissions. AWS provides a granular set of permissions that allow for precise control over resource access. For instance, instead of granting `s3:*`, grant `s3:GetObject` for specific objects in a bucket, or `dynamodb:GetItem` for a specific DynamoDB table.
- Testing and Validation: Deploy the Lambda function with the identified permissions and test it thoroughly. Monitor the function’s logs and any error messages to identify any missing permissions. Iterate on the permission set, adding or removing permissions as needed, until the function operates correctly with the minimum necessary access.
- Regular Review and Updates: As the function’s code evolves or its requirements change, regularly review and update the permissions. This is especially important when adding new features or integrating with new AWS services. Automated security scanning tools can help identify overly permissive IAM policies.
Analyzing Lambda Function Code for Resource Access
Analyzing the code is a fundamental step in identifying resource access requirements. This involves a systematic review of the function’s code to identify all interactions with AWS services. This analysis should be performed at the start of the development lifecycle and revisited whenever the code is modified.Consider these methods for code analysis:
- Manual Code Review: Carefully examine the function’s code, paying close attention to any calls to AWS SDKs (e.g., boto3 for Python, AWS SDK for JavaScript). Identify the AWS services being used, the API calls being made, and the resources being accessed. For example, if the function uses `s3.getObject()`, you know it needs permissions to read from S3.
- Dependency Analysis: Identify all dependencies imported by the function. These dependencies might themselves interact with AWS resources. For example, a library designed to process images may access S3 to retrieve images.
- Static Analysis Tools: Use static analysis tools, which can automatically scan the code and identify potential resource access patterns. These tools can help to identify common security issues, such as overly permissive IAM policies or the use of hardcoded credentials.
- Dynamic Analysis (Testing): Execute the Lambda function with various inputs and observe its behavior. Monitor the logs to identify any access denied errors or other permission-related issues. This provides valuable feedback to refine the permission set.
Checklist for Ensuring All Required Permissions Are Identified
Using a checklist ensures a systematic approach to identifying permissions, minimizing the risk of oversight and improving the security posture. The checklist should be used throughout the development and deployment lifecycle.This checklist is a valuable tool:
- Identify AWS Services: List all AWS services the Lambda function interacts with (e.g., S3, DynamoDB, CloudWatch Logs, API Gateway).
- Specify Resource ARNs: For each AWS service, specify the exact resources the function needs to access, using their Amazon Resource Names (ARNs). This includes buckets, tables, queues, and other resources.
- Define Required Actions: For each resource, list the specific API actions the function needs to perform (e.g., `s3:GetObject`, `dynamodb:PutItem`, `logs:CreateLogStream`).
- Review IAM Policies: Review the IAM policies attached to the Lambda function’s execution role. Ensure that the policies grant only the necessary permissions and no more.
- Test Functionality: Thoroughly test the Lambda function with different inputs and scenarios. Monitor logs for any permission errors.
- Regular Audits: Schedule regular audits of the function’s permissions to ensure they remain appropriate as the function evolves. Use tools to automatically check for over-permissioning.
- Least Privilege Enforcement: Ensure that the principle of least privilege is strictly adhered to, granting only the minimum permissions required for the function to operate correctly.
Structuring IAM Policies for Lambda Functions
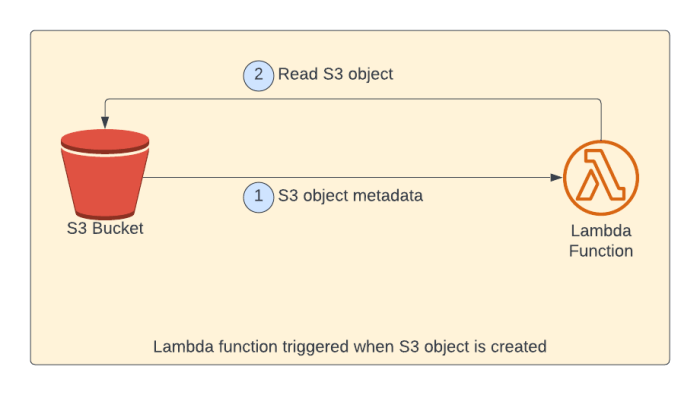
Crafting effective IAM policies is crucial for implementing the Principle of Least Privilege (PoLP) with Lambda functions. This involves meticulously defining the permissions a Lambda function requires to execute its tasks, ensuring it only has access to the resources it absolutely needs. A well-structured IAM policy not only enhances security by minimizing the attack surface but also simplifies auditing and troubleshooting.
The following sections detail best practices for structuring IAM policies for Lambda functions, including the use of policy variables and examples of minimal permissions for common use cases.
Best Practices for Writing IAM Policies for Lambda Functions
Adhering to best practices when writing IAM policies for Lambda functions is essential for maintaining a secure and efficient environment. These practices help minimize potential security risks and streamline the management of function permissions.
- Specify Resource-Level Permissions: Whenever possible, restrict access to specific resources rather than granting broad permissions. For example, instead of allowing access to all objects in an S3 bucket, specify the exact objects or prefixes the Lambda function needs to access. This significantly reduces the impact of a compromised function.
- Use the Principle of Least Privilege: Grant only the minimum necessary permissions. Avoid granting overly permissive permissions, such as `s3:*` for all S3 actions, unless absolutely required. Review and refine policies regularly to ensure they remain aligned with the function’s current needs.
- Employ Condition Keys: Utilize condition keys to further refine permissions based on context, such as the source IP address, the time of day, or the user initiating the request. This adds an extra layer of security and control.
- Regularly Review and Update Policies: Policies should be reviewed periodically to ensure they remain relevant and secure. As function requirements evolve, update the policies accordingly. Remove unnecessary permissions and add new ones only when necessary.
- Test Policies Thoroughly: Before deploying a policy, test it thoroughly to ensure it grants the intended permissions and blocks unintended access. Use the IAM Policy Simulator or AWS CloudTrail logs to validate the policy’s behavior.
- Leverage Managed Policies (When Appropriate): AWS provides managed policies for common use cases, such as allowing Lambda functions to access S3 or DynamoDB. Use these managed policies as a starting point and customize them to fit the specific needs of the function.
Demonstrating the Use of Policy Variables to Enhance the Flexibility and Security of IAM Policies
Policy variables are powerful tools that enhance the flexibility and security of IAM policies by allowing you to write policies that are applicable to multiple resources or users without requiring specific hardcoding of resource ARNs or user identities. This dynamic approach simplifies policy management and reduces the risk of errors.
Consider the use case of a Lambda function that needs to access objects in an S3 bucket. Instead of hardcoding the bucket ARN in the policy, you can use the $aws:username or $aws:userid variables to dynamically grant access based on the user’s identity or the function’s identity, respectively. This approach ensures that each function instance only accesses the specific resources it is authorized to access.
Here’s an example of using a policy variable within an IAM policy:
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Action": [ "s3:GetObject" ], "Resource": "arn:aws:s3:::my-bucket/$aws:username/*" ]
In this example, the Lambda function is granted permission to get objects from a specific path within the “my-bucket” S3 bucket.
The path is dynamically determined by the IAM user’s username. This policy ensures that each user or function, assuming proper identity management, can only access its designated objects within the bucket, adhering to the Principle of Least Privilege.
Creating a Table to Show Common Lambda Function Use Cases and Corresponding Minimal Permissions
The following table illustrates common Lambda function use cases and the minimal IAM permissions required for each. This table serves as a practical guide for designing secure and efficient IAM policies, demonstrating how to apply the Principle of Least Privilege in real-world scenarios.
| Use Case | AWS Service | Actions | Resource | Example Policy Snippet |
|---|---|---|---|---|
| Read data from S3 | S3 | s3:GetObject | arn:aws:s3:::your-bucket-name/your-object-prefix/* | "Effect": "Allow", "Action": [ "s3:GetObject" ], "Resource": "arn:aws:s3:::your-bucket-name/your-object-prefix/*" |
| Write data to S3 | S3 | s3:PutObject | arn:aws:s3:::your-bucket-name/your-object-prefix/* | "Effect": "Allow", "Action": [ "s3:PutObject" ], "Resource": "arn:aws:s3:::your-bucket-name/your-object-prefix/*" |
| Read data from DynamoDB | DynamoDB | dynamodb:GetItem, dynamodb:Query, dynamodb:Scan | arn:aws:dynamodb:*:*:table/your-table-name | "Effect": "Allow", "Action": [ "dynamodb:GetItem", "dynamodb:Query", "dynamodb:Scan" ], "Resource": "arn:aws:dynamodb:*:*:table/your-table-name" |
| Write data to DynamoDB | DynamoDB | dynamodb:PutItem | arn:aws:dynamodb:*:*:table/your-table-name | "Effect": "Allow", "Action": [ "dynamodb:PutItem" ], "Resource": "arn:aws:dynamodb:*:*:table/your-table-name" |
| Invoke another Lambda function | Lambda | lambda:InvokeFunction | arn:aws:lambda:*:*:function:your-other-function-name | "Effect": "Allow", "Action": [ "lambda:InvokeFunction" ], "Resource": "arn:aws:lambda:*:*:function:your-other-function-name" |
| Send messages to SQS | SQS | sqs:SendMessage | arn:aws:sqs:*:*:your-queue-name | "Effect": "Allow", "Action": [ "sqs:SendMessage" ], "Resource": "arn:aws:sqs:*:*:your-queue-name" |
| Publish messages to SNS | SNS | sns:Publish | arn:aws:sns:*:*:your-topic-name | "Effect": "Allow", "Action": [ "sns:Publish" ], "Resource": "arn:aws:sns:*:*:your-topic-name" |
| Log to CloudWatch Logs | CloudWatch Logs | logs:CreateLogGroup, logs:CreateLogStream, logs:PutLogEvents | arn:aws:logs:*:*:log-group:/aws/lambda/your-function-name | "Effect": "Allow", "Action": [ "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents" ], "Resource": "arn:aws:logs:*:*:log-group:/aws/lambda/your-function-name:*" |
Monitoring and Auditing Lambda Function Permissions
Effective monitoring and auditing are crucial components of maintaining the security posture of Lambda functions.
They provide insights into function behavior, access patterns, and potential security breaches. Regular monitoring allows for the proactive identification of anomalies, while robust auditing capabilities enable incident response and compliance adherence.
Importance of Monitoring Lambda Function Access and Activities
Monitoring Lambda function access and activities is essential for several reasons. It provides a real-time view of function execution, including invocations, errors, and resource utilization. This visibility helps detect unusual patterns that could indicate malicious activity or misconfigurations.
- Anomaly Detection: Monitoring allows for the identification of unexpected spikes in function invocations, unusual execution times, or errors that deviate from established baselines. For instance, a sudden increase in the number of invocations originating from an unfamiliar IP address could signal a denial-of-service (DoS) attack or unauthorized access.
- Performance Optimization: By monitoring resource consumption (e.g., memory, CPU) and execution duration, developers can identify performance bottlenecks and optimize function code or configurations. This ensures efficient resource utilization and cost management.
- Security Incident Response: Monitoring logs provide valuable data for investigating security incidents. They enable security teams to reconstruct the sequence of events leading to a breach, identify the compromised resources, and take appropriate remediation actions. For example, detailed logs can reveal which specific API calls were made, the data accessed, and the identity of the caller.
- Compliance and Governance: Monitoring helps organizations meet regulatory requirements and demonstrate compliance with security standards. Audit trails generated through monitoring can be used to verify that access controls are properly enforced and that sensitive data is protected.
Methods for Auditing IAM Policies to Identify Potential Security Vulnerabilities
Auditing IAM policies is a critical step in identifying and mitigating potential security vulnerabilities within the Lambda function environment. Regular reviews of IAM policies ensure that they adhere to the principle of least privilege and that access controls are appropriately configured.
- Policy Analysis Tools: Utilize automated tools and services provided by cloud providers or third-party vendors to analyze IAM policies. These tools can identify overly permissive policies, unused permissions, and potential security risks. For example, AWS IAM Access Analyzer can identify resources that are accessible from outside the organization.
- Policy Simulation: Employ policy simulation tools to assess the effective permissions granted by IAM policies. These tools allow you to simulate different scenarios and determine whether a given principal (e.g., user, role, function) can perform specific actions on specific resources. This helps identify unintended access and potential vulnerabilities.
- Regular Policy Reviews: Establish a schedule for regularly reviewing IAM policies. This should include both automated analysis and manual inspection by security professionals. The frequency of reviews should be determined based on the sensitivity of the data and the criticality of the functions.
- Version Control: Implement version control for IAM policies. This allows you to track changes to policies over time, revert to previous versions if necessary, and maintain an audit trail of policy modifications. This is essential for understanding how policies have evolved and identifying potential security regressions.
- Least Privilege Validation: Verify that each IAM policy adheres to the principle of least privilege. Ensure that policies grant only the minimum permissions required for the function to perform its intended tasks. Remove any unnecessary permissions and restrict access to specific resources and actions.
Setting Up CloudWatch Alarms to Detect Unauthorized Access Attempts
CloudWatch alarms are a valuable tool for detecting unauthorized access attempts and other security-related events within the Lambda function environment. They enable proactive monitoring and alerting, allowing security teams to respond quickly to potential threats.
- Monitoring Login Failures: Set up alarms to monitor for a high number of failed login attempts to the AWS console or other services used by Lambda functions. This could indicate an attempt to brute-force credentials or gain unauthorized access.
- Monitoring API Call Activity: Create alarms to detect unusual API call activity, such as an excessive number of calls to sensitive APIs (e.g., `PutObject` in S3, `CreateUser` in IAM) or calls from unexpected IP addresses or user agents.
- Monitoring Lambda Function Errors: Configure alarms to trigger when Lambda functions generate a high number of errors. This could indicate a misconfiguration, a denial-of-service attack, or an attempt to exploit a vulnerability.
- Monitoring Resource Access: Set up alarms to monitor access to sensitive resources used by Lambda functions, such as databases, S3 buckets, and KMS keys. Alert on any unauthorized access attempts or unusual access patterns.
- Example: Consider a scenario where a Lambda function accesses an S3 bucket containing sensitive customer data. A CloudWatch alarm can be configured to monitor for any `GetObject` calls to the bucket that originate from an unexpected source or that occur outside of normal business hours.
Least Privilege in Action: S3 Access Example
Implementing the Principle of Least Privilege (PoLP) with AWS Lambda functions is crucial for securing cloud resources. This example demonstrates a practical application of PoLP by configuring a Lambda function to interact with an Amazon S3 bucket, minimizing the permissions granted to it. The focus is on providing only the necessary access rights, adhering to the principle of granting the minimum privileges required for the function to perform its intended tasks.
Configuring Lambda Function S3 Access with Least Privilege
To configure a Lambda function for secure S3 access, a step-by-step procedure is necessary. This ensures the function operates with the fewest permissions required, reducing the potential attack surface.
- Create an IAM Role for the Lambda Function: This role defines the permissions the Lambda function will have. The role should be created with a trust relationship that allows the Lambda service to assume the role.
- Define an IAM Policy for S3 Access: This policy specifies the exact S3 actions the Lambda function is permitted to perform. It is essential to be precise with the actions and resources allowed.
- Attach the Policy to the IAM Role: The IAM policy is attached to the IAM role created in the first step. This grants the Lambda function the permissions defined in the policy.
- Configure the Lambda Function: When creating or updating the Lambda function, specify the IAM role created in the first step. This links the function to the permissions defined in the attached policy.
- Test the Function: Thoroughly test the Lambda function to ensure it can perform its intended tasks with the granted permissions. Verify that it cannot perform actions outside the defined permissions.
Demonstrating Specific S3 Actions in IAM Policy
The IAM policy is the core of implementing least privilege. It precisely defines the actions a Lambda function is allowed to perform on S3 resources. Specific S3 actions must be included in the policy to grant the required access.
The following is an example of an IAM policy that allows a Lambda function to only get and put objects within a specific S3 bucket:
“`json
“Version”: “2012-10-17”,
“Statement”: [
“Effect”: “Allow”,
“Action”: [
“s3:GetObject”,
“s3:PutObject”
],
“Resource”: “arn:aws:s3:::your-bucket-name/*”
]
“`
This policy grants the following permissions:
- `s3:GetObject`: Allows the function to retrieve objects from the specified S3 bucket.
- `s3:PutObject`: Allows the function to upload objects to the specified S3 bucket.
- `Resource`: Specifies the S3 bucket and objects that the permissions apply to, using the ARN (Amazon Resource Name) format. The `*` wildcard allows access to all objects within the bucket. For more restrictive access, you could specify the ARN of specific objects.
This example demonstrates granting only the necessary actions, adhering to the PoLP. It’s crucial to replace `”your-bucket-name”` with the actual name of the S3 bucket. If the function only needs to get objects, then `s3:PutObject` should be omitted.
Visual Representation of the S3 Access Flow
The access flow for the S3 example can be visually represented to illustrate the interaction between the Lambda function, the IAM role, the IAM policy, and the S3 bucket. This representation clarifies how the permissions are applied and how access is granted.
The visual representation can be described as follows:
1. Lambda Function (Initiator): The Lambda function, triggered by an event (e.g., an API Gateway request or an S3 event), initiates an action to interact with an S3 bucket.
2. IAM Role (Identity): The Lambda function assumes an IAM role that has been assigned to it during creation or configuration. This role provides the function with the necessary permissions to access AWS resources.
The role acts as the function’s identity within AWS.
3. IAM Policy (Permissions): The IAM role has an attached IAM policy. This policy explicitly defines the permissions the function has. The policy in this example specifies `s3:GetObject` and `s3:PutObject` actions, allowing the function to read and write objects within a specific S3 bucket.
The policy’s `Resource` element defines the scope of these permissions, typically targeting a specific S3 bucket or a set of objects within the bucket.
4. S3 Service (Resource): The Lambda function, acting under the IAM role and adhering to the IAM policy, interacts with the S3 service. If the action is `GetObject`, the function retrieves data from S3. If the action is `PutObject`, the function uploads data to S3.
The service validates the action against the permissions defined in the IAM policy associated with the role.
5. Access Granted/Denied (Decision Point): The S3 service evaluates the request against the IAM policy. If the action is permitted (e.g., `GetObject` or `PutObject` on the specified bucket), the request is granted, and the function can access the requested S3 resource. If the action is not permitted (e.g., attempting to delete an object without the `s3:DeleteObject` permission), the request is denied.
6. Data Flow (Direction): Data flows between the Lambda function and the S3 bucket, facilitated by the permissions granted through the IAM role and policy. The flow direction depends on the action (e.g., read from S3 or write to S3).
This visual representation clearly illustrates how the Lambda function’s access is controlled by the IAM role and policy, and how the S3 service enforces these permissions, which is a critical aspect of least privilege.
Least Privilege and Database Access
Implementing the Principle of Least Privilege (PoLP) is crucial when Lambda functions interact with databases. Restricting access to only the necessary permissions minimizes the attack surface and protects sensitive data. This section explores how to apply PoLP to database interactions, focusing on specific permissions and providing code examples.
Implementing PoLP for Database Interactions
The core principle is to grant Lambda functions only the precise permissions they require to perform their designated tasks. This involves careful planning and analysis of the function’s database interactions. Over-permissioning, where a function has broader access than needed, is a significant security risk.
Specific Permissions for Database Operations
Database operations require specific permissions, varying depending on the database type and the actions performed. Understanding these permissions is fundamental to implementing PoLP effectively. The following list Artikels common database operations and their corresponding permissions:
- Read Operations: These involve retrieving data from the database. Permissions required include:
- DynamoDB: `dynamodb:GetItem`, `dynamodb:Scan`, `dynamodb:Query`, `dynamodb:BatchGetItem`.
- RDS (e.g., PostgreSQL, MySQL): `SELECT` on specific tables or views.
- Write Operations: These involve modifying data in the database. Permissions required include:
- DynamoDB: `dynamodb:PutItem`, `dynamodb:UpdateItem`, `dynamodb:DeleteItem`, `dynamodb:BatchWriteItem`.
- RDS: `INSERT`, `UPDATE`, `DELETE` on specific tables.
- Update Operations: These involve modifying existing data. This often requires a combination of read and write permissions. Permissions required include:
- DynamoDB: `dynamodb:UpdateItem`.
- RDS: `UPDATE` on specific tables.
- Create Operations: Creating new resources within the database. Permissions required include:
- DynamoDB: `dynamodb:CreateTable` (for table creation).
- RDS: `CREATE TABLE` (for table creation), potentially other `CREATE` privileges depending on the database system (e.g., `CREATE USER`, `CREATE DATABASE`).
- Delete Operations: Removing resources from the database. Permissions required include:
- DynamoDB: `dynamodb:DeleteItem`.
- RDS: `DELETE` on specific tables.
Code Snippets for Granting Minimal Database Access
The following code snippets illustrate how to grant minimal database access to a Lambda function using AWS Identity and Access Management (IAM). These examples focus on granting access to specific DynamoDB tables and RDS resources. Note that these examples use the AWS CLI and assume you have configured your AWS credentials.
- DynamoDB Example: Granting read access to a specific DynamoDB table.
“`bash
aws iam put-role-policy \
–role-name\
–policy-name DynamoDBReadPolicy \
–policy-document ‘
“Version”: “2012-10-17”,
“Statement”: [“Effect”: “Allow”,
“Action”: [
“dynamodb:GetItem”,
“dynamodb:Scan”,
“dynamodb:Query”,
“dynamodb:BatchGetItem”
],
“Resource”: “arn:aws:dynamodb:: :table/ “
]
‘
“`In this example, replace `
`, ` `, ` `, and ` ` with the appropriate values. This policy grants read-only access to the specified DynamoDB table.
- DynamoDB Example: Granting write access to a specific DynamoDB table.
“`bash
aws iam put-role-policy \
–role-name\
–policy-name DynamoDBWritePolicy \
–policy-document ‘
“Version”: “2012-10-17”,
“Statement”: [“Effect”: “Allow”,
“Action”: [
“dynamodb:PutItem”,
“dynamodb:UpdateItem”,
“dynamodb:DeleteItem”,
“dynamodb:BatchWriteItem”
],
“Resource”: “arn:aws:dynamodb:: :table/ “
]
‘
“`Similar to the previous example, replace the placeholders. This policy grants write-only access to the specified DynamoDB table.
- RDS Example: Granting `SELECT` permission on a specific RDS database table.
“`sql
— Assuming you’re using PostgreSQL, adjust the syntax for other database systems
GRANT SELECT ONTO
;
“`This SQL statement grants the `SELECT` privilege to a user ( `
` ) who is assumed to be associated with the Lambda function via an IAM role. The IAM role needs to be configured to allow access to the RDS instance, which typically involves setting up the security group to allow access from the Lambda function’s VPC. The Lambda function must then connect to the database using the ` `’s credentials. - RDS Example: Granting `INSERT`, `UPDATE`, and `DELETE` permission on a specific RDS database table.
“`sql
— Assuming you’re using PostgreSQL, adjust the syntax for other database systems
GRANT INSERT, UPDATE, DELETE ONTO
;
“`This SQL statement grants the `INSERT`, `UPDATE`, and `DELETE` privileges to a user ( `
` ) who is assumed to be associated with the Lambda function via an IAM role.
Tools and Techniques for Implementing PoLP
Implementing the Principle of Least Privilege (PoLP) effectively requires a strategic approach, leveraging specialized tools and techniques to analyze permissions, automate policy management, and enforce security best practices. These tools streamline the process, reduce manual effort, and enhance the overall security posture of Lambda functions.
Using AWS CloudTrail and AWS IAM Access Analyzer for Permission Analysis
Analyzing existing permissions and identifying areas for improvement is crucial. AWS CloudTrail and AWS IAM Access Analyzer provide valuable insights into permission usage and potential security vulnerabilities.
AWS CloudTrail captures API calls made in your AWS account, providing a detailed history of actions taken. This information is invaluable for understanding how Lambda functions are interacting with other AWS services. By analyzing CloudTrail logs, you can determine:
- The specific AWS services and resources accessed by a Lambda function.
- The API calls made by the function.
- The success or failure of these API calls, which can indicate permission issues.
For example, imagine a Lambda function designed to process images stored in an S3 bucket. CloudTrail logs would reveal the specific S3 operations performed by the function (e.g., `GetObject`, `PutObject`, `ListBucket`). Analyzing these logs would allow you to confirm the function only has the necessary permissions, like read access to the image bucket and write access to a processing output bucket, and to remove any unnecessary permissions.
AWS IAM Access Analyzer helps identify unused or overly permissive access in your AWS environment. It analyzes your IAM policies and provides findings about external access to your resources and resources that can be accessed by other accounts or the internet. This service simplifies the process of identifying potential security risks by:
- Detecting overly permissive policies that grant more access than necessary.
- Identifying unused permissions that can be safely removed.
- Highlighting potential security vulnerabilities related to public or cross-account access.
IAM Access Analyzer can analyze IAM roles, service roles, and resource-based policies, providing detailed findings and recommendations for remediation. It can also identify situations where an IAM role is granted broad access, such as the `AdministratorAccess` policy, which is a significant security risk.
By combining the insights from CloudTrail and IAM Access Analyzer, you can build a comprehensive understanding of your Lambda function’s permission needs and optimize your IAM policies to adhere to the PoLP.
Using Infrastructure as Code (IaC) Tools to Automate IAM Policy Management
Automating IAM policy management is critical for maintaining consistency, reducing manual errors, and streamlining the deployment process. Infrastructure as Code (IaC) tools enable you to define your infrastructure, including IAM policies, in code, which can then be version-controlled, reviewed, and deployed automatically. Popular IaC tools such as Terraform and AWS CloudFormation are suitable for managing IAM policies.
Terraform is a popular IaC tool that allows you to define your infrastructure using declarative configuration files. It supports a wide range of AWS resources, including IAM roles and policies. You can define the IAM role for your Lambda function, specify the necessary permissions, and deploy the configuration using Terraform’s command-line interface.
For example, a Terraform configuration file might include the following code snippet to create an IAM policy that grants a Lambda function read access to an S3 bucket:
“`terraform
resource “aws_iam_policy” “lambda_s3_read_policy”
name = “lambda_s3_read_policy”
description = “Policy to allow Lambda function to read from S3 bucket”
policy = jsonencode(
Version = “2012-10-17”
Statement = [
Action = [
“s3:GetObject”,
]
Effect = “Allow”
Resource = “arn:aws:s3:::your-bucket-name/*”
,
]
)
resource “aws_iam_role_policy_attachment” “lambda_s3_read_attachment”
role = aws_iam_role.lambda_role.name
policy_arn = aws_iam_policy.lambda_s3_read_policy.arn
“`
This code defines an IAM policy that allows `s3:GetObject` actions on all objects within the specified S3 bucket. The policy is then attached to the IAM role associated with the Lambda function.
AWS CloudFormation is an AWS-native IaC tool that allows you to define your infrastructure using YAML or JSON templates. CloudFormation provides a declarative approach to infrastructure management, allowing you to define your resources and their dependencies in a single template.
A CloudFormation template for an IAM role might include the following:
“`yaml
Resources:
LambdaExecutionRole:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Version: ‘2012-10-17’
Statement:
-Effect: Allow
Principal:
Service: lambda.amazonaws.com
Action: sts:AssumeRole
Policies:
-PolicyName: LambdaS3ReadPolicy
PolicyDocument:
Version: ‘2012-10-17’
Statement:
-Effect: Allow
Action:
-s3:GetObject
Resource:
-arn:aws:s3:::your-bucket-name/*
“`
This CloudFormation template defines an IAM role that allows the Lambda service to assume the role and grants the role permission to perform the `s3:GetObject` action on objects in the specified S3 bucket.
Using IaC tools for IAM policy management offers several benefits:
- Version control: IaC code can be stored in a version control system, allowing you to track changes, roll back to previous versions, and collaborate with others.
- Automation: IaC tools automate the deployment and management of IAM policies, reducing manual effort and the risk of human error.
- Consistency: IaC ensures that IAM policies are consistently applied across your infrastructure, reducing the likelihood of configuration drift.
- Auditing: IaC provides a clear audit trail of changes to your IAM policies, simplifying compliance and security audits.
Best Practices for Automated IAM Policy Enforcement
- Define policies as code: Use IaC tools to define IAM policies in code, enabling version control, automation, and consistency.
- Use least privilege principles: Grant only the minimum necessary permissions required for each Lambda function.
- Automate policy validation: Integrate automated testing and validation into your CI/CD pipeline to ensure that IAM policies meet security requirements.
- Regularly review and update policies: Periodically review your IAM policies to ensure they remain aligned with your security requirements and business needs.
- Implement automated alerts: Configure alerts to notify you of any unauthorized changes to IAM policies or suspicious activity.
The Evolution of PoLP in Lambda Functions

The principle of least privilege (PoLP) has undergone significant evolution within the context of AWS Lambda functions, driven by advancements in AWS services and a growing emphasis on security best practices. This evolution reflects a shift towards more granular control, automated enforcement, and a deeper understanding of the attack surface in serverless environments.
Latest Advancements and Features Supporting PoLP
AWS continuously introduces features that enhance the implementation of PoLP for Lambda functions. These features aim to provide developers with finer-grained control over permissions and streamline the security management process.
- Resource-Based Policies: Lambda now supports resource-based policies, allowing developers to explicitly define which AWS services or accounts can invoke a specific Lambda function. This is crucial for scenarios where functions are triggered by events from other services (e.g., S3, API Gateway). By restricting the services and accounts that can trigger a function, the attack surface is reduced. For example, a resource-based policy could be used to ensure that only a specific API Gateway is authorized to invoke a particular Lambda function.
- IAM Condition Keys: IAM condition keys enable the creation of highly specific policies. They allow developers to restrict access based on factors like the source IP address, the time of day, or the user agent. For instance, a Lambda function accessing S3 could have its access restricted to only requests originating from a specific VPC or subnet. This enhances security by preventing unauthorized access even if the function’s IAM role is compromised.
- Lambda Function URLs: Function URLs provide a dedicated HTTPS endpoint for Lambda functions, simplifying invocation and integration with other services. When used in conjunction with IAM, function URLs offer another layer of access control. You can restrict access to a Function URL using IAM policies, ensuring that only authenticated users or specific services can invoke the function through the URL.
- AWS CloudTrail Integration: CloudTrail logs all API calls made to Lambda functions, including those related to permission changes. This enables detailed auditing and monitoring of permission modifications, allowing security teams to detect and respond to unauthorized access attempts or misconfigurations.
- IAM Access Analyzer: IAM Access Analyzer helps identify overly permissive IAM policies by analyzing resource-based policies and IAM policies. It flags potential security risks, such as functions that grant unnecessary access to other AWS resources. This tool streamlines the process of identifying and remediating overly broad permissions.
Security Implications of Different Lambda Function Runtimes
The choice of Lambda function runtime can significantly impact the security posture and, consequently, the application of PoLP. Different runtimes have varying dependencies, vulnerabilities, and levels of control over the execution environment.
- Managed Runtimes (e.g., Node.js, Python, Java): These runtimes are pre-configured and managed by AWS. They offer a balance between ease of use and security. However, vulnerabilities within the runtime itself can impact security. The permissions granted to the Lambda function’s IAM role are critical, as any exploit of a runtime vulnerability could potentially leverage those permissions. Regular patching and updates of the runtime environment by AWS are crucial to mitigating risks.
- Custom Runtimes (e.g., using container images): Using container images allows for greater control over the runtime environment, including the operating system and installed packages. This can be advantageous for implementing more stringent security measures. However, it also increases the responsibility of the developer to maintain the security of the container image. Incorrectly configured or outdated container images can introduce significant security risks. The application of PoLP is crucial in containerized Lambda functions, as the IAM role’s permissions must be carefully aligned with the container’s needs.
- Runtime Environment Security Considerations: The underlying operating system and libraries within a runtime are potential attack vectors. Vulnerabilities in these components can be exploited to gain unauthorized access or escalate privileges. For example, a vulnerability in a Python library used by a Lambda function could be exploited if the function’s IAM role has excessive permissions. Proper dependency management, regular security scanning, and the application of PoLP are critical to mitigating these risks.
Future Trends and Potential Improvements in Implementing PoLP in Serverless Architectures
The future of PoLP in serverless architectures promises even more sophisticated and automated mechanisms for enforcing least privilege. These trends aim to reduce the burden on developers and enhance the overall security posture of serverless applications.
- Automated Policy Generation: AI-powered tools could automatically generate IAM policies based on the function’s code, dependencies, and interactions with other AWS services. These tools could analyze the function’s behavior and suggest the minimum necessary permissions, significantly reducing the risk of overly permissive policies.
- Dynamic Permission Management: Lambda functions could dynamically request and release permissions based on their immediate needs. This would involve fine-grained control over permissions, where the function only has access to the resources it requires at the moment of execution. This would require a secure mechanism for requesting and revoking permissions at runtime.
- Zero Trust Architectures: Implementing zero-trust principles in serverless environments involves verifying every request and granting access based on the principle of least privilege. This could involve integrating identity and access management with advanced authentication and authorization mechanisms, such as multi-factor authentication and continuous authorization.
- Policy-as-Code and Infrastructure-as-Code: Integrating IAM policies with infrastructure-as-code tools (e.g., Terraform, AWS CloudFormation) and policy-as-code frameworks would enable automated deployment and enforcement of PoLP across the entire serverless infrastructure. This would improve consistency and reduce the risk of human error.
- Enhanced Monitoring and Anomaly Detection: Advanced monitoring tools could detect anomalies in function behavior, such as unexpected resource access or unusual API calls. These tools could then trigger alerts and automatically adjust permissions to mitigate potential security threats. For instance, if a Lambda function starts accessing an S3 bucket it has never accessed before, the system could flag this as suspicious activity.
Final Wrap-Up
In conclusion, mastering the Principle of Least Privilege for Lambda functions is not merely a best practice; it’s a fundamental requirement for building secure and resilient serverless applications. By meticulously defining permissions, employing robust monitoring techniques, and staying abreast of evolving security features, developers can significantly reduce the attack surface and mitigate potential security risks. The ongoing evolution of serverless technologies necessitates a continuous focus on PoLP, ensuring that our applications remain secure in the face of emerging threats.
Implementing PoLP is a dynamic process, requiring constant vigilance and adaptation to maintain the integrity and confidentiality of our serverless architectures.
FAQ Guide
What happens if a Lambda function is over-permissioned?
An over-permissioned Lambda function grants more access than it needs, increasing the potential attack surface. If compromised, an attacker could use the function’s permissions to access sensitive data, modify resources, or launch further attacks within your AWS environment.
How can I determine the exact permissions a Lambda function requires?
Analyze the function’s code to identify the resources it interacts with (e.g., S3 buckets, DynamoDB tables). Use tools like AWS CloudTrail to monitor the function’s access patterns and identify the specific actions it performs. Start with a restrictive policy and gradually add permissions as needed, testing after each addition.
What are the differences between managed and inline IAM policies?
Managed policies are created and managed by AWS or by you, and can be attached to multiple IAM roles. Inline policies are created and managed directly within an IAM role and are specific to that role. Inline policies offer more granular control but are harder to manage at scale.
How can I automate IAM policy management?
Use Infrastructure as Code (IaC) tools like Terraform or CloudFormation to define and manage your IAM policies. IaC allows you to version control your policies, automate their deployment, and ensure consistency across your environment. Consider using tools like AWS IAM Access Analyzer to check your policies.
What is the impact of Lambda function runtimes on permissions?
Different Lambda runtimes might have varying levels of resource access based on their underlying environment. Newer runtimes and those with specific dependencies could require additional permissions to function correctly. Always review the runtime’s documentation and test the function’s behavior with minimal permissions.