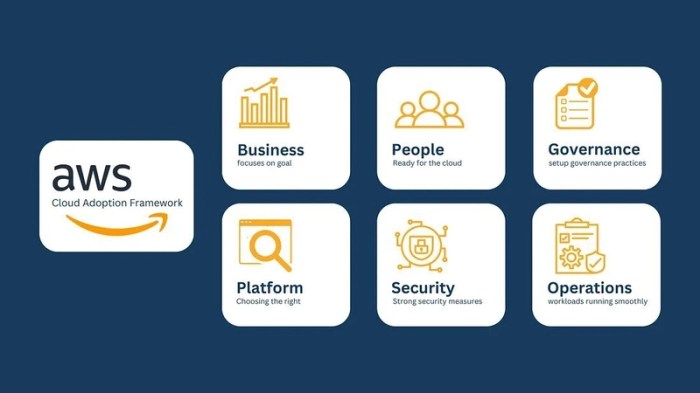
The AWS Cloud Adoption Framework (CAF) provides a structured methodology for organizations embarking on or optimizing their cloud journey. This framework, encompassing five key perspectives—Business, People, Governance, Platform, and Security—offers a comprehensive roadmap to navigate the complexities of cloud adoption. Understanding and applying the CAF is crucial for aligning cloud initiatives with business objectives, managing organizational change, establishing robust governance, designing efficient platforms, and ensuring a secure cloud environment.
By leveraging the CAF, organizations can mitigate risks, accelerate innovation, and realize the full potential of the cloud.
This exploration delves into each perspective of the CAF, providing insights into its goals, key considerations, and practical implementation strategies. From aligning cloud strategies with business goals to optimizing financial performance and fostering a cloud-first culture, the CAF empowers organizations to make informed decisions. We’ll examine how to assess your current state, create a strategic roadmap, and navigate the various phases of cloud adoption, including mobilization, migration, and modernization.
Furthermore, we will explore essential tools, resources, and success metrics to guide you toward a successful and sustainable cloud transformation.
Introduction to the AWS Cloud Adoption Framework (CAF)
The AWS Cloud Adoption Framework (CAF) provides a structured approach to guide organizations through their cloud adoption journey. It’s a strategic framework designed to help businesses build and execute effective cloud strategies, accelerating their cloud adoption and maximizing its benefits. By providing a comprehensive methodology, the CAF helps organizations align their business and IT strategies, identify and address potential challenges, and ultimately achieve their desired business outcomes.
Core Purpose of the AWS CAF
The primary purpose of the AWS CAF is to assist organizations in successfully adopting cloud technologies. It serves as a blueprint, offering guidance and best practices for all aspects of cloud adoption, from planning and strategy to implementation and ongoing management. The framework aims to ensure that cloud adoption aligns with business goals, enabling organizations to improve agility, reduce costs, and drive innovation.
The CAF facilitates a structured approach, minimizing risks and maximizing the potential of cloud computing. It focuses on:
- Accelerating cloud adoption by providing a clear roadmap.
- Improving business agility and responsiveness.
- Reducing operational costs through optimized resource utilization.
- Driving innovation by leveraging cloud-native services.
- Ensuring alignment between business and IT strategies.
The Five Perspectives of the CAF
The AWS CAF is organized around five key perspectives, each representing a critical area of focus for successful cloud adoption. These perspectives are interconnected and should be addressed holistically to achieve optimal results. Each perspective provides a set of considerations, best practices, and recommendations to guide organizations in their cloud journey.
- Business Perspective: This perspective focuses on aligning cloud adoption with business strategies and outcomes. It involves understanding business goals, identifying key performance indicators (KPIs), and defining the value proposition of cloud adoption. The business perspective ensures that cloud initiatives support overall business objectives, such as revenue growth, market expansion, and customer satisfaction. It addresses questions like: “How will cloud adoption improve our business outcomes?”
- People Perspective: The people perspective addresses the human element of cloud adoption, focusing on organizational structure, skills, and culture. It involves identifying the skills gaps, training needs, and organizational changes required to support cloud initiatives. This perspective ensures that the organization has the right talent and capabilities to effectively manage and utilize cloud services. Key considerations include talent acquisition, skills development, and organizational change management.
- Governance Perspective: This perspective focuses on establishing the processes and mechanisms to manage and control cloud environments. It involves defining policies, standards, and procedures for cloud usage, including cost management, security, and compliance. The governance perspective ensures that cloud resources are used efficiently, securely, and in accordance with organizational policies. It addresses questions such as: “How do we control cloud costs?” and “How do we ensure compliance with regulatory requirements?”
- Platform Perspective: The platform perspective focuses on the technical aspects of cloud adoption, including infrastructure, applications, and data. It involves selecting the appropriate cloud services, designing the cloud architecture, and implementing the necessary tools and technologies. This perspective ensures that the organization’s cloud environment is scalable, reliable, and secure. Key considerations include network design, compute resources, storage solutions, and database management.
- Security Perspective: The security perspective focuses on protecting cloud resources and data from threats. It involves implementing security controls, establishing security policies, and monitoring the cloud environment for vulnerabilities. This perspective ensures that the organization’s cloud environment is secure and compliant with industry best practices. Key considerations include identity and access management, data encryption, and threat detection and response.
How the CAF Helps Organizations Navigate Cloud Adoption Challenges
The AWS CAF provides a structured methodology to address the challenges organizations face during cloud adoption. By applying the framework’s guidance, organizations can proactively identify and mitigate potential risks, streamline their cloud initiatives, and maximize the benefits of cloud computing. The CAF helps organizations overcome common hurdles, such as:
- Lack of Clear Strategy: The CAF helps organizations define a clear cloud strategy aligned with their business goals.
- Skills Gaps: The CAF provides guidance on identifying skills gaps and developing training programs to address them.
- Security Concerns: The CAF offers best practices for implementing security controls and ensuring data protection.
- Cost Management Challenges: The CAF provides recommendations for managing cloud costs and optimizing resource utilization.
- Compliance Requirements: The CAF helps organizations navigate compliance requirements and ensure adherence to industry standards.
The Business Perspective
The Business Perspective within the AWS Cloud Adoption Framework (CAF) focuses on aligning cloud initiatives with overall business strategy and achieving desired business outcomes. It ensures that cloud adoption is driven by business needs, leading to increased value realization and improved strategic agility. This perspective considers financial, operational, and strategic aspects to guide cloud adoption decisions.
Key Goals and Outcomes
The primary goals of the Business Perspective are to maximize business value from cloud adoption, ensuring alignment with strategic objectives. This involves understanding the business drivers for cloud adoption and establishing clear outcomes that contribute to organizational success.
- Strategic Alignment: Ensures cloud initiatives directly support and advance the organization’s strategic goals, such as market expansion, innovation, or increased customer satisfaction.
- Value Realization: Defines and tracks the expected business value from cloud adoption, including revenue growth, cost reduction, and improved efficiency.
- Business Agility: Enables the organization to respond quickly to market changes, innovate rapidly, and adapt to evolving customer needs.
- Risk Management: Identifies and mitigates business-related risks associated with cloud adoption, such as regulatory compliance, security, and data privacy.
- Financial Optimization: Optimizes cloud spending to maximize return on investment (ROI) and minimize costs.
Aligning Cloud Initiatives with Business Strategy
Aligning cloud initiatives with business strategy requires a structured approach to ensure that cloud adoption supports the organization’s overall goals. This involves a thorough understanding of the business strategy and translating strategic objectives into actionable cloud initiatives.
- Strategic Assessment: Conduct a comprehensive assessment of the current business strategy, including market analysis, competitive landscape, and organizational goals.
- Identify Business Drivers: Determine the specific business drivers that will be supported by cloud adoption, such as cost reduction, increased agility, or improved customer experience.
- Define Business Outcomes: Establish clear, measurable, achievable, relevant, and time-bound (SMART) business outcomes that align with the strategic goals.
- Prioritize Cloud Initiatives: Prioritize cloud initiatives based on their potential impact on the defined business outcomes and their alignment with the strategic goals.
- Governance and Oversight: Establish governance structures and processes to ensure that cloud initiatives remain aligned with the business strategy and that progress is tracked and reported regularly.
For example, a retail company aiming to expand its e-commerce operations might adopt cloud services to handle increased website traffic during peak seasons. The business driver is to improve customer experience and increase sales, with the business outcome being a 20% increase in online revenue within one year.
Financial Considerations: Cost Optimization
Financial considerations are central to the Business Perspective, with cost optimization being a critical aspect. This involves managing cloud spending effectively to maximize ROI and minimize unnecessary costs. A proactive approach to cost optimization ensures that cloud resources are used efficiently and that spending aligns with business needs.
- Cost Visibility and Monitoring: Implement tools and processes to monitor cloud spending in real-time, providing visibility into resource utilization and cost trends.
- Right-Sizing Resources: Ensure that cloud resources are appropriately sized to meet the demands of the workload, avoiding over-provisioning and unnecessary costs.
- Reserved Instances and Savings Plans: Utilize reserved instances and savings plans to obtain discounted pricing for predictable workloads.
- Automation and Optimization: Automate resource management and optimization processes to reduce manual effort and improve efficiency.
- Cost Allocation and Chargeback: Implement cost allocation and chargeback mechanisms to track cloud spending by department, project, or business unit, enabling better cost management.
For instance, a software-as-a-service (SaaS) company could use AWS Cost Explorer to analyze its cloud spending, identify underutilized resources, and optimize its instance sizes, leading to significant cost savings. By implementing these strategies, the company can reduce its cloud spending by 15% within six months.
Key Performance Indicators (KPIs) for Measuring Business Success
Measuring the success of cloud adoption requires the establishment of relevant KPIs that track progress toward achieving the defined business outcomes. These KPIs provide insights into the value realized from cloud adoption and enable data-driven decision-making.
| KPI | Description | Measurement Method | Target |
|---|---|---|---|
| Revenue Growth | Percentage increase in revenue attributed to cloud-enabled initiatives. | Track revenue before and after cloud adoption, comparing the difference. | 10% annual increase |
| Cost Reduction | Percentage decrease in IT infrastructure and operational costs. | Compare IT costs before and after cloud adoption. | 15% reduction in IT costs |
| Time-to-Market | Reduction in the time it takes to launch new products or services. | Measure the time from concept to launch before and after cloud adoption. | 20% reduction in time-to-market |
| Customer Satisfaction | Improvement in customer satisfaction scores, such as Net Promoter Score (NPS). | Conduct customer surveys before and after cloud adoption. | Increase NPS by 10 points |
The People Perspective
The People Perspective of the AWS Cloud Adoption Framework (CAF) focuses on the organizational structures, skills, and processes necessary to support cloud adoption. It addresses the human element of the cloud journey, ensuring that the workforce is prepared and equipped to effectively leverage cloud technologies. This perspective aims to foster a cloud-first culture by addressing the required changes in skills, roles, and organizational structures.
Roles and Responsibilities in Cloud Adoption
Cloud adoption necessitates a clearly defined set of roles and responsibilities to ensure accountability and effective execution. These roles often transcend traditional IT departments and require collaboration across various business units. The following are common roles involved in cloud adoption, along with their key responsibilities:
- Executive Sponsor: Provides strategic direction and overall support for cloud initiatives. They are responsible for securing budget, aligning cloud strategy with business goals, and advocating for cloud adoption at the highest levels of the organization. Their involvement is crucial for driving organizational change and overcoming resistance.
- Cloud Architect: Designs and oversees the cloud infrastructure, ensuring it meets the organization’s technical requirements, security standards, and cost optimization goals. They are responsible for selecting appropriate cloud services, designing network architecture, and implementing best practices for cloud deployments. Cloud Architects need to possess a deep understanding of cloud technologies and the ability to translate business needs into technical solutions.
- Cloud Security Engineer: Focuses on securing cloud environments, implementing security controls, and ensuring compliance with relevant regulations. They are responsible for identifying and mitigating security risks, managing access control, and monitoring security events. Cloud Security Engineers require expertise in cloud security best practices, threat detection, and incident response.
- Cloud Operations Engineer: Manages the day-to-day operations of cloud infrastructure, including monitoring, automation, and troubleshooting. They are responsible for ensuring the availability and performance of cloud resources, automating routine tasks, and responding to incidents. Cloud Operations Engineers need to be proficient in cloud monitoring tools, automation scripts, and infrastructure-as-code practices.
- Cloud Developer: Develops and deploys applications on the cloud platform. They are responsible for writing code, integrating with cloud services, and ensuring application performance and scalability. Cloud Developers need to be skilled in cloud-native development practices, including microservices, serverless computing, and DevOps methodologies.
- Cloud Financial Analyst: Manages cloud spending, optimizes costs, and provides financial reporting. They are responsible for tracking cloud expenses, identifying cost-saving opportunities, and forecasting future cloud spending. Cloud Financial Analysts need to be proficient in cloud cost management tools and techniques, as well as possess strong analytical skills.
- Business Analyst: Works with business stakeholders to identify opportunities for cloud adoption and translate business requirements into technical solutions. They are responsible for gathering requirements, conducting feasibility studies, and ensuring that cloud initiatives align with business objectives. Business Analysts need to have a strong understanding of both business processes and cloud technologies.
Skills and Training for Cloud Adoption
Successful cloud adoption requires a workforce equipped with the necessary skills and knowledge. Investing in training and development is crucial for ensuring employees can effectively utilize cloud technologies and drive innovation. The following are key areas for skills development:
- Cloud Fundamentals: Understanding of core cloud concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). This includes a foundational knowledge of cloud computing models, benefits, and challenges.
- Cloud Security: Proficiency in cloud security best practices, including identity and access management (IAM), data encryption, and threat detection. This involves understanding security frameworks, compliance requirements, and security tools.
- Cloud Architecture: Ability to design and implement cloud solutions that meet business requirements. This involves understanding cloud service offerings, architectural patterns, and best practices for cloud deployments.
- Cloud Operations: Skills in managing and operating cloud infrastructure, including monitoring, automation, and troubleshooting. This includes proficiency in cloud management tools and infrastructure-as-code practices.
- Cloud Development: Expertise in developing and deploying applications on the cloud platform. This involves skills in cloud-native development practices, including microservices, serverless computing, and DevOps methodologies.
- Data Analytics and Machine Learning: Ability to leverage cloud-based data analytics and machine learning services to extract insights from data. This involves proficiency in data warehousing, data processing, and machine learning algorithms.
- Soft Skills: Effective communication, collaboration, and problem-solving skills are crucial for successful cloud adoption. These skills facilitate teamwork, knowledge sharing, and the ability to adapt to changing circumstances.
Training programs should be tailored to the specific roles and responsibilities within the organization. This might include formal training courses, online learning platforms, hands-on workshops, and on-the-job training. Organizations can also consider partnering with cloud providers to leverage their training resources and certification programs. For example, AWS offers a comprehensive range of training and certification programs designed to equip individuals with the skills needed to succeed in cloud environments.
Organizational Change Management Plan
Cloud migration represents a significant organizational change that requires a well-defined change management plan to minimize disruption and maximize the benefits of cloud adoption. A successful plan includes the following key components:
- Assess Readiness: Evaluate the organization’s current state, including its culture, skills, and processes, to identify potential challenges and opportunities. This assessment should involve stakeholder interviews, surveys, and data analysis to understand the organization’s readiness for change.
- Define the Vision: Clearly articulate the goals and benefits of cloud adoption to align stakeholders and build support. The vision should communicate the “why” behind the cloud initiative, emphasizing the value it will bring to the organization.
- Develop a Communication Plan: Create a comprehensive communication plan to keep stakeholders informed throughout the migration process. The plan should include regular updates, town hall meetings, and training sessions to address concerns and build momentum.
- Provide Training and Support: Offer training programs and support resources to equip employees with the skills and knowledge needed to succeed in the cloud environment. This includes providing access to documentation, online resources, and hands-on training.
- Manage Resistance to Change: Identify and address potential resistance to change by proactively communicating the benefits of cloud adoption and addressing concerns. This may involve providing additional training, addressing job security concerns, and involving employees in the decision-making process.
- Measure and Monitor Progress: Track key metrics to measure the success of the cloud migration and make adjustments as needed. This includes monitoring adoption rates, cost savings, and performance improvements.
A well-executed change management plan can significantly improve the likelihood of a successful cloud migration. For example, a study by McKinsey & Company found that organizations with strong change management practices are significantly more likely to achieve their cloud migration goals. The study emphasizes the importance of addressing the human element of cloud adoption, including communication, training, and stakeholder engagement.
Fostering a Cloud-First Culture
A cloud-first culture encourages the proactive adoption of cloud technologies and fosters a mindset of innovation and agility. Cultivating such a culture involves a multi-faceted approach:
- Leadership Commitment: Executive leadership must champion cloud adoption and demonstrate a commitment to investing in cloud technologies and training. This includes setting clear goals, providing resources, and celebrating successes.
- Cloud-Focused Teams: Establish dedicated cloud teams with clear responsibilities and empowered to make decisions. These teams should be cross-functional, including representatives from various business units and IT departments.
- Training and Enablement: Invest in comprehensive training programs to equip employees with the skills and knowledge needed to leverage cloud technologies. This should include both technical training and soft skills development.
- Cloud-Native Development Practices: Encourage the adoption of cloud-native development practices, such as DevOps, continuous integration and continuous delivery (CI/CD), and microservices. This enables faster development cycles and improved agility.
- Cloud-First Policies and Guidelines: Develop clear policies and guidelines that promote cloud adoption, such as a cloud-first approach to new projects and a preference for cloud-based solutions.
- Collaboration and Knowledge Sharing: Foster a culture of collaboration and knowledge sharing by encouraging employees to share their experiences, best practices, and lessons learned. This can be achieved through internal forums, communities of practice, and knowledge-sharing platforms.
- Incentives and Recognition: Recognize and reward employees who champion cloud adoption and demonstrate innovation. This can include offering incentives for completing cloud certifications, participating in cloud projects, and sharing knowledge.
For example, Netflix has a strong cloud-first culture, leveraging AWS extensively to support its streaming services. This culture is driven by a commitment to innovation, agility, and continuous improvement. Netflix encourages its engineers to experiment with new technologies, adopt DevOps practices, and embrace a “fail fast, learn fast” approach. This culture has enabled Netflix to rapidly scale its services, adapt to changing market conditions, and maintain its position as a leader in the streaming industry.
The Governance Perspective
Effective cloud governance is paramount for successful cloud adoption, ensuring that cloud resources are used efficiently, securely, and in alignment with business objectives. It provides the framework for managing risk, controlling costs, and maintaining compliance throughout the cloud journey. Without robust governance, organizations risk uncontrolled sprawl, security vulnerabilities, and difficulties in meeting regulatory requirements.
Importance of Governance in Cloud Adoption
Cloud governance establishes the foundation for sustainable cloud operations. It provides the necessary controls to manage cloud resources, mitigate risks, and optimize performance. By implementing governance, organizations can achieve several key benefits.
- Cost Optimization: Governance enables organizations to track and control cloud spending, identify waste, and optimize resource utilization. For example, using AWS Cost Explorer, organizations can analyze their spending patterns, identify opportunities for savings (e.g., unused instances, rightsizing), and implement cost allocation tags to understand spending by department or project.
- Security and Compliance: Governance helps to define and enforce security policies, ensuring data protection and compliance with industry regulations (e.g., HIPAA, GDPR). AWS Config and AWS Security Hub provide tools to monitor configurations, detect security vulnerabilities, and automate remediation.
- Operational Efficiency: Governance streamlines cloud operations by automating tasks, standardizing processes, and providing centralized management. Infrastructure as Code (IaC) tools, such as AWS CloudFormation, allow organizations to define and deploy infrastructure consistently and repeatably.
- Risk Management: Governance frameworks help identify and mitigate potential risks associated with cloud adoption, such as data breaches, service disruptions, and compliance violations. Regular audits, vulnerability assessments, and incident response plans are crucial components of a robust risk management strategy.
- Alignment with Business Goals: Governance ensures that cloud initiatives align with the overall business strategy. This involves defining clear roles and responsibilities, establishing decision-making processes, and regularly reviewing cloud performance against business objectives.
Methods for Establishing Policies and Procedures for Cloud Resource Management
Establishing effective policies and procedures is crucial for managing cloud resources efficiently and securely. This involves defining clear guidelines, automating processes, and providing appropriate training to cloud users. Several methods can be employed to achieve this.
- Define Cloud Governance Framework: A cloud governance framework Artikels the principles, policies, and procedures that govern cloud usage. This framework should address key areas such as security, cost management, access control, and compliance. The framework should be tailored to the organization’s specific needs and risk profile.
- Implement Access Control Policies: Access control policies define who can access cloud resources and what actions they can perform. Role-Based Access Control (RBAC) is a common approach, allowing administrators to assign permissions based on user roles and responsibilities. AWS Identity and Access Management (IAM) provides granular control over access to AWS resources.
- Establish Resource Tagging Strategy: Resource tagging involves applying metadata to cloud resources, enabling organizations to categorize and manage resources effectively. Tags can be used for cost allocation, resource tracking, and automation. A consistent tagging strategy is essential for effective governance. For example, tags such as `CostCenter`, `Environment` (e.g., `Production`, `Development`), and `Owner` can provide valuable insights into resource usage and ownership.
- Automate Resource Provisioning: Automating resource provisioning reduces manual effort, minimizes errors, and ensures consistency. Infrastructure as Code (IaC) tools, such as AWS CloudFormation and Terraform, allow organizations to define infrastructure as code, enabling automated deployment and management.
- Implement Cost Management Strategies: Cost management strategies help organizations control cloud spending. This includes setting budgets, monitoring costs, identifying waste, and optimizing resource utilization. AWS Cost Explorer, AWS Budgets, and AWS Trusted Advisor provide tools and insights for effective cost management.
- Enforce Security Policies: Security policies define the security requirements for cloud resources. This includes defining security baselines, implementing security controls, and monitoring security events. AWS Security Hub and AWS Config provide tools for monitoring security posture and enforcing security policies.
- Regularly Review and Update Policies: Cloud environments are dynamic, so governance policies must be regularly reviewed and updated to reflect changing business needs, security threats, and regulatory requirements. This ensures that policies remain effective and relevant.
Managing Risk and Compliance within the Governance Perspective
Risk and compliance management are integral components of cloud governance. Organizations must identify, assess, and mitigate risks associated with cloud adoption and ensure compliance with relevant regulations. This requires a proactive approach and the implementation of appropriate controls.
- Risk Assessment: A risk assessment identifies potential risks associated with cloud usage. This involves evaluating the likelihood and impact of various threats, such as data breaches, service disruptions, and compliance violations. The risk assessment should inform the development of risk mitigation strategies.
- Compliance Management: Compliance management ensures that cloud resources comply with relevant regulations and industry standards. This involves identifying applicable regulations, implementing necessary controls, and conducting regular audits. AWS provides services and tools to help organizations meet compliance requirements.
- Incident Response Planning: An incident response plan Artikels the steps to be taken in the event of a security incident or service disruption. The plan should define roles and responsibilities, communication protocols, and remediation procedures. Regular testing of the incident response plan is essential.
- Data Protection: Data protection is a critical aspect of cloud governance. This involves implementing measures to protect data confidentiality, integrity, and availability. Encryption, access controls, and data backup and recovery strategies are essential components of a data protection plan.
- Continuous Monitoring: Continuous monitoring involves monitoring cloud resources for security vulnerabilities, performance issues, and compliance violations. AWS CloudWatch and AWS Security Hub provide tools for monitoring and alerting on various metrics.
- Third-Party Risk Management: Organizations should assess the risks associated with third-party vendors that provide cloud services or access cloud resources. This includes evaluating the vendor’s security posture, compliance certifications, and incident response capabilities.
- Regular Audits: Regular audits are essential for verifying the effectiveness of governance policies and controls. Audits should be conducted by qualified personnel and should cover areas such as security, compliance, and cost management.
Best Practices for Implementing Cloud Governance Policies
Implementing effective cloud governance policies requires a strategic approach and a commitment to continuous improvement. Adhering to best practices can help organizations achieve their cloud governance objectives.
- Start with a Pilot Project: Before implementing governance policies across the entire organization, start with a pilot project to test and refine the policies. This allows organizations to identify and address any issues before a full-scale rollout.
- Automate as Much as Possible: Automate governance tasks, such as resource provisioning, security configuration, and cost management. Automation reduces manual effort, minimizes errors, and ensures consistency.
- Use Infrastructure as Code (IaC): Use IaC tools to define and deploy infrastructure consistently and repeatably. This simplifies infrastructure management and enables version control.
- Implement a Centralized Logging and Monitoring System: Implement a centralized logging and monitoring system to collect and analyze logs from cloud resources. This helps organizations identify security threats, performance issues, and compliance violations.
- Establish a Cloud Center of Excellence (CCoE): A CCoE provides a centralized team responsible for defining and enforcing cloud governance policies. The CCoE can also provide training and support to cloud users.
- Provide Regular Training: Provide regular training to cloud users on governance policies, security best practices, and cost management strategies. This ensures that users are aware of their responsibilities and can use cloud resources effectively.
- Document Everything: Document all governance policies, procedures, and configurations. This provides a clear understanding of the governance framework and facilitates audits and troubleshooting.
- Foster a Culture of Collaboration: Foster a culture of collaboration between IT, security, finance, and business stakeholders. This ensures that governance policies are aligned with business objectives and that all stakeholders are engaged in the cloud governance process.
- Continuously Review and Improve: Cloud environments are constantly evolving, so governance policies must be continuously reviewed and improved. Regularly assess the effectiveness of governance policies and make adjustments as needed.
The Platform Perspective
The Platform Perspective within the AWS Cloud Adoption Framework (CAF) focuses on the technical underpinnings of cloud adoption, encompassing the design and operation of the infrastructure and services that support workloads. This perspective considers how to build, operate, and optimize the platform, ensuring it aligns with business needs and technical requirements.
Infrastructure Design and Deployment Strategies
Infrastructure design and deployment strategies are crucial for building a robust and scalable cloud platform. These strategies determine how resources are provisioned, managed, and updated.
- Infrastructure as Code (IaC): IaC allows infrastructure to be defined and managed using code, enabling automation, version control, and repeatability. AWS CloudFormation and Terraform are examples of IaC tools. A practical example is defining an entire network stack (VPC, subnets, security groups, etc.) as a CloudFormation template, allowing for consistent deployments across multiple environments. This approach reduces manual configuration errors and accelerates deployment times.
- Automation: Automation streamlines repetitive tasks, such as server provisioning, software updates, and scaling. AWS provides services like AWS Systems Manager and AWS Lambda for automation. For instance, using Lambda functions to automatically patch EC2 instances based on defined schedules or trigger actions in response to events.
- Containerization: Containerization, using technologies like Docker and orchestration platforms like Amazon Elastic Container Service (ECS) or Amazon Elastic Kubernetes Service (EKS), packages applications with their dependencies, ensuring consistent behavior across different environments. This improves portability and simplifies deployment. A real-world example is deploying a microservices-based application on ECS, where each service is containerized and managed by ECS for scaling and availability.
- Serverless Computing: Serverless computing allows developers to build and run applications without managing servers. AWS Lambda is a key serverless service. This approach reduces operational overhead and enables auto-scaling based on demand. A common use case is building a web application backend using Lambda functions triggered by API Gateway requests, automatically scaling up or down based on the number of requests.
- High Availability and Disaster Recovery: Designing for high availability involves creating systems that are resilient to failures and can continue operating even when components fail. Disaster recovery plans ensure that data can be recovered and applications can be restored in case of a major outage. AWS provides services like Amazon Route 53 for DNS failover, Amazon S3 for data replication, and AWS Backup for data protection.
Implementing a multi-AZ (Availability Zone) architecture for critical applications ensures high availability.
AWS Services within the Platform Perspective
The Platform Perspective leverages various AWS services to build and manage the cloud infrastructure. These services cover compute, storage, networking, database, and security aspects.
- Compute: AWS offers various compute services, including Amazon Elastic Compute Cloud (EC2) for virtual machines, Amazon Elastic Container Service (ECS) and Amazon Elastic Kubernetes Service (EKS) for container orchestration, and AWS Lambda for serverless computing. For example, EC2 instances can be used to host web servers or application servers, while Lambda functions can be used to process data or trigger workflows.
- Storage: AWS provides a range of storage options, including Amazon Simple Storage Service (S3) for object storage, Amazon Elastic Block Storage (EBS) for block storage, and Amazon Elastic File System (EFS) for file storage. S3 is often used for storing backups, static website content, or data lakes. EBS volumes are attached to EC2 instances for persistent storage, while EFS provides shared file storage for multiple instances.
- Networking: Amazon Virtual Private Cloud (VPC) allows users to create isolated networks within the AWS cloud. Other networking services include Amazon Route 53 for DNS, Elastic Load Balancing (ELB) for distributing traffic, and AWS Direct Connect for establishing dedicated network connections. A VPC enables users to control network traffic, configure security groups, and manage network access.
- Database: AWS offers various database services, including Amazon Relational Database Service (RDS) for managed relational databases, Amazon DynamoDB for NoSQL databases, and Amazon Aurora for MySQL and PostgreSQL-compatible databases. RDS simplifies database management tasks like patching and backups. DynamoDB provides high-performance, scalable NoSQL database capabilities.
- Security: AWS provides a comprehensive suite of security services, including AWS Identity and Access Management (IAM) for managing user access, Amazon Virtual Private Cloud (VPC) security groups and network access control lists (ACLs) for network security, AWS Key Management Service (KMS) for encryption, and AWS Web Application Firewall (WAF) for protecting web applications. IAM policies control user permissions, and security groups act as virtual firewalls for EC2 instances.
Serverless computing provides several key benefits:
- Reduced Operational Overhead: Eliminates the need to manage servers, operating systems, and patching.
- Automatic Scaling: Automatically scales resources based on demand, eliminating the need for manual capacity planning.
- Cost Efficiency: Pay-per-use pricing model, which means you only pay for the compute time consumed.
- Increased Agility: Enables faster development cycles and quicker time-to-market.
The Security Perspective
The Security Perspective within the AWS Cloud Adoption Framework (CAF) provides a structured approach to integrating security best practices throughout the cloud adoption journey. It focuses on establishing a robust security posture that aligns with business objectives, regulatory requirements, and risk tolerance. This perspective emphasizes the importance of proactive security measures, continuous monitoring, and incident response planning to protect data, applications, and infrastructure in the cloud.
Security Considerations Within the AWS CAF
The Security Perspective considers several key areas crucial for establishing a secure cloud environment. These considerations ensure that security is not an afterthought but is embedded within every stage of cloud adoption.
- Data Security: Focuses on protecting data at rest and in transit through encryption, access controls, and data loss prevention (DLP) strategies. This includes implementing encryption keys, managing data classification, and enforcing data governance policies.
- Infrastructure Security: Addresses the security of the underlying infrastructure, including network security, server security, and endpoint protection. This involves configuring firewalls, intrusion detection/prevention systems (IDS/IPS), and vulnerability management tools.
- Identity and Access Management (IAM): Establishes secure access controls through the management of user identities, roles, and permissions. This encompasses multi-factor authentication (MFA), least privilege access, and regular access reviews.
- Compliance and Governance: Ensures adherence to relevant industry regulations and internal policies. This involves implementing compliance frameworks, automating security audits, and establishing governance processes.
- Incident Response: Defines the processes and procedures for detecting, responding to, and recovering from security incidents. This includes creating incident response plans, establishing communication channels, and conducting regular incident response drills.
- Security Automation: Emphasizes the automation of security tasks, such as vulnerability scanning, configuration management, and security incident remediation. This helps to improve efficiency, reduce human error, and accelerate response times.
Best Practices for Implementing Security Controls in the Cloud
Implementing robust security controls in the cloud requires a strategic approach that aligns with AWS best practices. These best practices are designed to provide a layered defense-in-depth strategy.
- Implement Identity and Access Management (IAM) Best Practices: Employ least privilege access, multi-factor authentication (MFA), and regularly review and audit IAM policies. For example, enforce MFA for all privileged accounts to mitigate the risk of compromised credentials.
- Employ Network Security Controls: Utilize Virtual Private Clouds (VPCs) with network segmentation, security groups, and network access control lists (ACLs) to control network traffic. Configure a Web Application Firewall (WAF) to protect against common web exploits, and use intrusion detection and prevention systems (IDS/IPS) to monitor for malicious activity.
- Utilize Encryption: Encrypt data at rest and in transit using encryption keys managed by AWS Key Management Service (KMS) or other solutions. Regularly rotate encryption keys to minimize the impact of potential key compromises.
- Implement Data Loss Prevention (DLP): Employ DLP solutions to monitor and prevent sensitive data from leaving the cloud environment. Define data classification policies and use automated tools to identify and protect sensitive data.
- Automate Security Monitoring and Incident Response: Use AWS CloudWatch, AWS Security Hub, and other security monitoring tools to collect and analyze security logs and events. Automate incident response procedures to rapidly mitigate security threats. For example, use AWS Lambda functions to automatically quarantine compromised instances.
- Regularly Patch and Update Systems: Maintain up-to-date operating systems, applications, and security software to address known vulnerabilities. Implement automated patching processes to ensure systems are patched in a timely manner.
- Conduct Regular Security Audits and Penetration Testing: Regularly audit the cloud environment to identify security vulnerabilities and compliance gaps. Conduct penetration testing to simulate real-world attacks and validate the effectiveness of security controls.
The Role of Identity and Access Management (IAM) in Cloud Security
Identity and Access Management (IAM) is a cornerstone of cloud security, providing the foundation for controlling access to AWS resources. Effective IAM implementation minimizes the attack surface and reduces the risk of unauthorized access and data breaches.
- Centralized Identity Management: IAM enables the centralized management of user identities, roles, and permissions. This simplifies the process of managing access across multiple AWS services.
- Least Privilege Access: IAM allows for the implementation of the principle of least privilege, granting users only the necessary permissions to perform their tasks. This limits the potential impact of a compromised account.
- Multi-Factor Authentication (MFA): IAM supports the use of MFA, adding an extra layer of security to user accounts. This makes it significantly more difficult for attackers to gain unauthorized access.
- Access Control Policies: IAM provides granular control over access to AWS resources through the use of policies. These policies define what actions users or roles can perform on specific resources.
- Auditing and Monitoring: IAM integrates with AWS CloudTrail to provide detailed audit logs of all API calls made within the AWS environment. This allows for the monitoring of user activity and the detection of suspicious behavior.
- Integration with Enterprise Identity Providers: IAM supports integration with existing enterprise identity providers, such as Active Directory or Okta, allowing organizations to leverage their existing identity infrastructure for cloud access management.
Security Responsibilities Across Different Teams
A collaborative approach to security is essential for effectively managing cloud security. The following table details the security responsibilities across different teams within an organization.
| Team | Responsibilities | Examples | Tools and Technologies |
|---|---|---|---|
| Executive Leadership | Establish security strategy, policies, and risk tolerance. Ensure adequate resources are allocated for security. | Approving security budgets, setting security objectives, and reviewing security reports. | Security frameworks (e.g., NIST, ISO 27001), risk management tools, and board reporting dashboards. |
| Security Team | Develop and implement security policies, monitor security posture, and respond to security incidents. Manage IAM, network security, and data protection. | Conducting vulnerability assessments, managing security configurations, and responding to security alerts. | AWS Security Hub, Amazon GuardDuty, intrusion detection/prevention systems (IDS/IPS), SIEM solutions. |
| Development/Engineering Team | Implement secure coding practices, integrate security controls into applications, and address security vulnerabilities in code. | Using secure coding standards, performing code reviews, and integrating security testing into the CI/CD pipeline. | Static and dynamic code analysis tools, container security tools, and security libraries. |
| Operations Team | Maintain infrastructure security, configure and manage security tools, and ensure compliance with security policies. Monitor system performance and availability. | Managing network configurations, implementing patching and updates, and monitoring system logs. | Configuration management tools (e.g., AWS Systems Manager), monitoring tools (e.g., CloudWatch), and incident response platforms. |
Planning Your Cloud Adoption Journey
Successfully navigating the AWS Cloud Adoption Framework (CAF) requires a well-defined plan. This involves understanding your current operational landscape, envisioning your future state, and meticulously charting a course to achieve your cloud adoption goals. A strategic roadmap is crucial for prioritizing initiatives, managing resources effectively, and mitigating potential risks throughout the transition.
Assessing Current State and Defining Desired Future State
A thorough assessment of your current IT environment is the foundational step in cloud adoption planning. This evaluation provides a baseline understanding of your existing infrastructure, applications, security posture, and operational processes. Simultaneously, defining your desired future state involves articulating your strategic objectives, outlining the benefits you expect to realize from cloud adoption, and establishing key performance indicators (KPIs) to measure success.The assessment process should encompass several key areas:
- Business Alignment: Evaluate how IT supports business goals, including current and planned initiatives. Identify areas where cloud adoption can enhance business agility, reduce costs, and improve time-to-market. For example, if a company aims to expand into a new market, the cloud’s scalability and global reach can facilitate rapid deployment of applications and services in the target region.
- Technology Infrastructure: Inventory existing hardware, software, and network components. Analyze their performance, utilization, and dependencies. Determine the compatibility of existing systems with cloud services and identify potential migration strategies. This involves assessing server configurations, storage solutions, and network architectures.
- People and Skills: Evaluate the skills and experience of your IT staff. Identify any skill gaps that need to be addressed through training or hiring. Consider the organizational structure and roles related to cloud operations. For example, if a company is heavily reliant on on-premises database administrators, it must develop or acquire expertise in cloud-based database services like Amazon RDS or Amazon Aurora.
- Processes and Governance: Document existing IT processes, including change management, incident response, and security protocols. Evaluate their suitability for a cloud environment. Establish cloud governance policies, including cost management, security compliance, and access control.
- Security and Compliance: Assess your current security posture, including data protection, access controls, and vulnerability management. Identify relevant compliance requirements, such as HIPAA, PCI DSS, or GDPR. Develop a cloud security strategy that addresses these requirements.
Defining the desired future state requires articulating specific goals and objectives. These might include:
- Increased Agility: Improve the speed and flexibility of IT operations. This could involve automating deployment processes, enabling self-service provisioning, and scaling resources on demand.
- Reduced Costs: Optimize IT spending by leveraging cloud pricing models, eliminating capital expenditures, and reducing operational overhead. This involves analyzing current IT costs, identifying areas for optimization, and estimating the potential cost savings from cloud adoption.
- Enhanced Innovation: Enable the development and deployment of new applications and services. Cloud platforms offer a wide range of services and tools that can accelerate innovation.
- Improved Scalability: Ensure that IT resources can scale up or down to meet changing business demands. Cloud services provide virtually unlimited scalability, allowing organizations to handle peak loads and growth without significant upfront investment.
- Enhanced Security: Improve the security posture by leveraging the security features of cloud platforms and implementing robust security controls.
The desired future state should be documented with specific, measurable, achievable, relevant, and time-bound (SMART) goals. For example, instead of a general goal like “reduce costs,” a SMART goal might be “reduce IT infrastructure costs by 20% within the next 12 months by migrating specific workloads to the cloud.”
Creating a Cloud Adoption Roadmap
A cloud adoption roadmap provides a structured plan for migrating to the cloud. It Artikels the specific steps, timelines, and resources required to achieve your cloud adoption goals. This roadmap serves as a guiding document, helping to manage expectations, track progress, and ensure alignment across the organization.The roadmap development process includes the following steps:
- Define Scope and Objectives: Clearly define the scope of the cloud adoption initiative, including the specific applications, workloads, or business units that will be migrated. Reiterate the strategic objectives and desired outcomes.
- Prioritize Workloads: Assess and prioritize workloads based on factors such as business value, technical complexity, and migration effort. This involves categorizing workloads based on their criticality, dependencies, and suitability for cloud migration.
- Select Migration Strategy: Choose the appropriate migration strategy for each workload. Common strategies include rehosting (lift and shift), re-platforming, refactoring, repurchasing, and retaining. The selection depends on the workload’s characteristics, business requirements, and available resources.
- Develop Migration Plan: Create a detailed migration plan for each workload, including specific tasks, timelines, and resource assignments. This plan should include pre-migration activities (e.g., assessment, planning), migration execution, and post-migration validation.
- Establish Governance and Controls: Implement cloud governance policies and controls to manage costs, security, and compliance. This includes establishing processes for access management, cost monitoring, and incident response.
- Develop a Training Plan: Develop a training plan to upskill the IT staff with the necessary cloud skills. This plan should identify the training needs, select training providers, and establish a schedule for training.
- Execute and Monitor: Execute the migration plan, monitoring progress and making adjustments as needed. Use KPIs to track performance and measure the success of the migration.
- Iterate and Optimize: Continuously evaluate the cloud environment and optimize performance, cost, and security. This includes regularly reviewing resource utilization, implementing cost optimization strategies, and updating security controls.
A well-defined roadmap should include a timeline, resource allocation, and a risk management plan. The timeline should Artikel the key milestones and deadlines for each phase of the cloud adoption journey. Resource allocation should specify the personnel, budget, and tools required. The risk management plan should identify potential risks, such as data loss, security breaches, or cost overruns, and Artikel mitigation strategies.
Designing a Framework for Prioritizing Cloud Adoption Initiatives
Prioritizing cloud adoption initiatives is crucial for maximizing the value and minimizing the risks of cloud migration. A robust framework provides a systematic approach to evaluating and ranking potential projects, ensuring that resources are allocated to the most impactful initiatives.The framework should consider several factors:
- Business Value: Assess the potential business benefits of each initiative, such as increased revenue, reduced costs, improved customer satisfaction, or enhanced agility. Quantify the expected benefits whenever possible.
- Technical Feasibility: Evaluate the technical complexity of each initiative, including the compatibility of existing systems with cloud services, the availability of required skills, and the potential for integration with other systems.
- Risk Assessment: Identify and assess the potential risks associated with each initiative, such as data loss, security breaches, or compliance violations. Develop mitigation strategies to address these risks.
- Cost Analysis: Estimate the costs associated with each initiative, including migration costs, ongoing operational costs, and potential cost savings. Compare the costs of cloud adoption with the costs of maintaining the existing infrastructure.
- Dependencies: Identify any dependencies between initiatives. Some initiatives may need to be completed before others can begin.
A common approach for prioritizing initiatives is to use a scoring system. Each initiative is evaluated against the criteria above, and a score is assigned for each criterion. The scores are then weighted based on their importance, and the initiatives are ranked based on their total scores.An example of a scoring system:
| Criterion | Weight | Scoring Range |
|---|---|---|
| Business Value | 40% | 1-5 (1 = Low, 5 = High) |
| Technical Feasibility | 25% | 1-5 (1 = Low, 5 = High) |
| Risk Assessment | 15% | 1-5 (1 = Low, 5 = High) |
| Cost Analysis | 20% | 1-5 (1 = Low, 5 = High) |
Each initiative is scored against each criterion, and the scores are multiplied by the weights to calculate a weighted score. The initiatives are then ranked based on their total weighted scores. This framework provides a data-driven approach to decision-making, ensuring that cloud adoption initiatives are prioritized based on their potential value and feasibility.
Illustrating the Cloud Adoption Journey Stages
The cloud adoption journey can be visualized as a series of stages, each representing a distinct phase of the transition. Understanding these stages provides a roadmap for planning and executing the migration.The stages typically include:
Diagram: The diagram depicts a circular journey with four main stages: Assess, Mobilize, Migrate, and Optimize.
Assess: This initial stage involves evaluating the current IT landscape, defining business goals, and creating a cloud adoption strategy. Activities include assessing the current state, defining the future state, and developing a business case.
Mobilize: This stage focuses on preparing the organization for cloud adoption. It includes building cloud skills, establishing governance policies, and setting up the cloud environment. Activities include training staff, establishing cloud governance, and setting up the cloud environment.
Migrate: This stage involves migrating applications and workloads to the cloud. It includes selecting the migration strategy, executing the migration plan, and validating the results. Activities include migrating workloads, validating migrations, and decommissioning on-premises resources.
Optimize: This final stage focuses on continuously improving the cloud environment. It includes monitoring performance, optimizing costs, and enhancing security. Activities include monitoring performance, optimizing costs, and enhancing security.
These stages are iterative, and organizations may revisit earlier stages as needed. The journey is not linear, and organizations may move back and forth between stages as they learn and adapt. This cyclical approach ensures continuous improvement and maximizes the benefits of cloud adoption.
Implementing the AWS CAF
The AWS Cloud Adoption Framework (CAF) provides a structured approach to cloud adoption, guiding organizations through various phases to achieve their desired business outcomes. Implementing the CAF involves a phased approach, with each phase encompassing specific activities, tools, and potential challenges. This structured methodology facilitates a smoother transition to the cloud, mitigating risks and optimizing the value derived from cloud investments.
Cloud Adoption Phases
The cloud adoption journey, as defined by the AWS CAF, typically unfolds through several distinct phases. Each phase represents a significant stage in the cloud transformation process, with defined objectives, activities, and expected outcomes. The phases are not necessarily linear, and organizations may iterate between them based on their specific needs and priorities.
Mobilize Phase
The Mobilize phase is the initial phase of cloud adoption. It focuses on establishing a clear vision, defining the scope of the cloud initiative, and building a foundation for future cloud deployments. This phase is crucial for setting the stage for a successful cloud transformation.
- Activities: The primary activities within the Mobilize phase include:
- Defining Business Outcomes: Identifying the specific business goals and objectives that cloud adoption will support. This involves understanding the “why” behind the cloud initiative and aligning it with overall business strategy.
- Building a Business Case: Quantifying the potential benefits of cloud adoption, including cost savings, increased agility, and improved innovation. This often involves a detailed analysis of current IT costs and projected cloud costs.
- Identifying Initial Workloads: Determining which applications and workloads are suitable for migration to the cloud. This involves assessing the complexity, dependencies, and business criticality of each workload.
- Developing a Cloud Strategy: Creating a high-level plan that Artikels the organization’s approach to cloud adoption, including governance, security, and operational models.
- Establishing a Cloud Center of Excellence (CCoE): Forming a dedicated team to guide and support cloud adoption efforts. The CCoE typically comprises representatives from various departments, such as IT, security, and finance.
- Tools and Technologies: Organizations utilize various tools and technologies during the Mobilize phase, including:
- AWS Cloud Adoption Readiness Tool (CART): Assists in assessing an organization’s readiness for cloud adoption across various dimensions, such as people, process, and technology.
- AWS Cost Explorer: Provides insights into current IT spending and helps estimate cloud costs.
- Business Case Modeling Tools: Used to build detailed business cases and quantify the benefits of cloud adoption.
- Project Management Software: Facilitates the planning and tracking of cloud adoption projects.
- Potential Challenges and Solutions: The Mobilize phase can present several challenges.
- Challenge: Lack of clear business objectives. Solution: Conduct workshops and interviews with key stakeholders to define specific, measurable, achievable, relevant, and time-bound (SMART) goals.
- Challenge: Difficulty building a comprehensive business case. Solution: Utilize AWS Cost Explorer and other tools to gather detailed cost data and conduct thorough analysis.
- Challenge: Resistance to change from stakeholders. Solution: Communicate the benefits of cloud adoption clearly and involve stakeholders in the planning process.
Migrate Phase
The Migrate phase focuses on moving existing workloads and applications to the cloud. This phase involves the actual transfer of data, applications, and infrastructure to the AWS environment. The success of the Migrate phase is critical to realizing the benefits of cloud adoption.
- Activities: The Migrate phase encompasses the following activities:
- Assessment and Planning: Conducting a detailed assessment of existing workloads to determine the optimal migration strategy (e.g., rehosting, replatforming, refactoring, repurchase, or retiring).
- Migration Execution: Performing the actual migration of workloads, which involves transferring data, configuring infrastructure, and testing applications.
- Validation and Optimization: Verifying that migrated workloads function correctly and optimizing them for performance and cost-efficiency in the cloud.
- Data Migration: Implementing a robust data migration strategy to ensure the integrity and availability of data during the migration process.
- Tools and Technologies: Organizations leverage various tools and technologies during the Migrate phase, including:
- AWS Migration Hub: Provides a central location to track and manage migration projects.
- AWS Application Discovery Service: Helps discover on-premises servers and applications to assess their suitability for migration.
- AWS Database Migration Service (DMS): Facilitates the migration of databases to AWS.
- AWS Server Migration Service (SMS): Simplifies the migration of on-premises servers to AWS.
- Third-Party Migration Tools: Such as CloudEndure, which provides block-level replication for migrating servers with minimal downtime.
- Potential Challenges and Solutions: The Migrate phase can present a number of challenges.
- Challenge: Downtime during migration. Solution: Utilize tools like AWS DMS and CloudEndure to minimize downtime. Employ phased migration strategies, migrating non-critical workloads first.
- Challenge: Complex dependencies between applications. Solution: Analyze application dependencies thoroughly and prioritize migration based on complexity. Break down monolithic applications into microservices.
- Challenge: Data transfer limitations. Solution: Utilize AWS Snowball or Snowmobile for large data transfers. Optimize network bandwidth.
Modernize Phase
The Modernize phase involves transforming applications to leverage the full potential of cloud-native services. This phase focuses on refactoring and rearchitecting applications to improve scalability, agility, and resilience. The Modernize phase represents a more advanced stage of cloud adoption.
- Activities: The Modernize phase involves the following activities:
- Application Assessment: Evaluating existing applications to identify opportunities for modernization.
- Refactoring and Re-architecting: Modifying applications to utilize cloud-native services, such as serverless computing, containerization, and managed databases.
- DevOps Implementation: Implementing DevOps practices to automate the software development lifecycle and accelerate the release of new features.
- Continuous Integration and Continuous Delivery (CI/CD): Establishing CI/CD pipelines to automate the build, testing, and deployment of applications.
- Tools and Technologies: Organizations use various tools and technologies during the Modernize phase, including:
- AWS CodePipeline: A fully managed CI/CD service that automates the software release process.
- AWS CodeBuild: A fully managed build service that compiles source code, runs tests, and produces software packages.
- AWS CodeDeploy: A fully managed deployment service that automates the deployment of applications to various compute services.
- AWS Lambda: A serverless compute service that allows you to run code without provisioning or managing servers.
- Amazon Elastic Container Service (ECS) and Amazon Elastic Kubernetes Service (EKS): Container orchestration services for running and managing containerized applications.
- AWS AppSync: A fully managed GraphQL service that simplifies the development of APIs.
- Potential Challenges and Solutions: The Modernize phase can present several challenges.
- Challenge: High initial investment and long development cycles. Solution: Start with small, incremental changes. Prioritize the modernization of high-impact applications. Use Agile methodologies.
- Challenge: Skills gap in cloud-native technologies. Solution: Invest in training and upskilling. Partner with cloud experts and consultants.
- Challenge: Complex application dependencies. Solution: Break down monolithic applications into microservices. Utilize service meshes.
Tools and Resources for AWS CAF Implementation
Effective implementation of the AWS Cloud Adoption Framework (CAF) requires leveraging a combination of AWS native services, third-party tools, and comprehensive documentation. This section provides an overview of the resources available to support each perspective of the CAF, ensuring a smooth and successful cloud adoption journey.
AWS Services Supporting the CAF
Several AWS services directly support the various perspectives of the Cloud Adoption Framework. Utilizing these services allows organizations to streamline their cloud adoption efforts, improve efficiency, and enhance overall governance.
- Business Perspective: Services like AWS Cost Explorer, AWS Budgets, and AWS Marketplace contribute to the Business Perspective by providing tools for cost management, financial planning, and evaluating third-party solutions. Cost Explorer visualizes spending trends, allowing for informed decisions based on financial data. AWS Budgets enables setting custom budget alerts to proactively manage costs. AWS Marketplace facilitates the discovery and procurement of pre-configured solutions that align with business requirements.
- People Perspective: AWS Training and Certification, coupled with AWS Skill Builder, directly address the People Perspective by providing training resources to upskill and reskill personnel. These resources enable organizations to develop the necessary cloud skills within their workforce. Furthermore, services like Amazon WorkDocs and Amazon Chime can facilitate collaboration and communication, supporting the cultural and organizational changes associated with cloud adoption.
- Governance Perspective: AWS CloudTrail, AWS Config, and AWS IAM are crucial for the Governance Perspective. CloudTrail logs API calls, providing audit trails for security and compliance. AWS Config enables resource configuration tracking and compliance checks. AWS IAM allows for the secure management of user access and permissions.
- Platform Perspective: Services such as Amazon EC2, Amazon S3, Amazon VPC, and AWS Lambda form the core of the Platform Perspective. EC2 provides scalable compute capacity, S3 offers object storage, VPC enables network isolation, and Lambda allows for serverless computing. These services provide the foundational building blocks for deploying and managing cloud infrastructure.
- Security Perspective: AWS Identity and Access Management (IAM), AWS Shield, AWS WAF, Amazon GuardDuty, and Amazon Inspector are fundamental to the Security Perspective. IAM manages user access and permissions. Shield provides DDoS protection. WAF protects against web application attacks. GuardDuty provides threat detection, and Inspector automates security assessments.
Third-Party Tools Complementing the CAF
While AWS offers a robust suite of services, third-party tools can further enhance the implementation of the CAF by providing specialized functionalities and integrations. These tools often cater to specific needs within each CAF perspective.
- Cost Management and Optimization: Tools like CloudHealth by VMware, Apptio, and CloudCheckr provide advanced cost optimization capabilities, allowing organizations to identify and eliminate waste, optimize resource utilization, and forecast future spending. They often integrate with AWS Cost Explorer and Budgets to provide more in-depth analytics and recommendations.
- DevOps and Automation: Solutions such as Terraform by HashiCorp, Ansible, and Chef facilitate infrastructure as code (IaC) and automation, streamlining the deployment and management of cloud resources. These tools help to improve agility and reduce manual effort, supporting the Platform Perspective.
- Security and Compliance: Tools like Splunk, Sumo Logic, and Rapid7 InsightVM provide security information and event management (SIEM), vulnerability scanning, and compliance monitoring capabilities. These solutions integrate with AWS security services to provide a comprehensive security posture.
- Application Performance Monitoring (APM): New Relic, Datadog, and Dynatrace offer APM solutions that provide insights into application performance, helping organizations to identify and resolve performance bottlenecks and optimize application deployments.
Relevant AWS Documentation and Resources
AWS provides extensive documentation, whitepapers, and other resources to guide organizations through the cloud adoption process and support the implementation of the CAF.
- AWS Cloud Adoption Framework (CAF) Whitepaper: The official whitepaper provides a detailed overview of the CAF, including its perspectives, best practices, and guidance for implementation.
- AWS Well-Architected Framework: This framework provides guidance on designing and operating reliable, secure, efficient, cost-effective, and sustainable systems in the cloud. It aligns with the CAF and provides practical recommendations for each perspective.
- AWS Documentation: The AWS documentation website offers comprehensive information on all AWS services, including tutorials, API references, and best practices.
- AWS Solutions Library: The Solutions Library provides pre-built solutions for common use cases, accelerating cloud adoption and reducing the need for custom development.
- AWS Blogs: The AWS blogs offer insights, best practices, and announcements related to cloud computing and AWS services.
- AWS Training and Certification: This program provides training courses and certifications to help individuals and organizations develop the skills needed to succeed in the cloud.
Using AWS CloudFormation for Infrastructure as Code
AWS CloudFormation allows you to model and set up your AWS resources so you can spend less time managing those resources and more time focusing on your applications that run in AWS. It uses a declarative approach, allowing you to define your infrastructure in a template and then deploy it consistently.
Here’s an example demonstrating how to create an S3 bucket using CloudFormation:
Template (YAML):
AWSTemplateFormatVersion: '2010-09-09'Description: 'Creates an S3 bucket'Resources: MyS3Bucket: Type: 'AWS::S3::Bucket' Properties: BucketName: 'my-unique-bucket-name-12345' # Replace with a globally unique bucket name AccessControl: PublicRead # Adjust access control as needed Explanation:
- AWSTemplateFormatVersion: Specifies the template version.
- Description: Provides a description of the template.
- Resources: Defines the AWS resources to be created.
- MyS3Bucket: Logical ID of the S3 bucket.
- Type: Specifies the resource type (AWS::S3::Bucket).
- Properties: Defines the properties of the S3 bucket.
- BucketName: Specifies the bucket name (must be globally unique).
- AccessControl: Sets the access control policy (e.g., PublicRead, Private).
Deployment:
To deploy this template, you would use the AWS Management Console, AWS CLI, or AWS SDKs. During deployment, CloudFormation creates the S3 bucket based on the defined configuration.
Benefits of using CloudFormation:
- Infrastructure as Code: Allows you to define your infrastructure in code, enabling version control, reusability, and automation.
- Repeatability: Ensures consistent deployments across different environments.
- Idempotency: CloudFormation manages the state of your resources, ensuring that changes are applied only when necessary.
- Rollback: Automatically rolls back to a previous state if a deployment fails.
Measuring Success and Continuous Improvement
Measuring the success of cloud adoption efforts is crucial for validating the investment, identifying areas for improvement, and ensuring alignment with business objectives. A robust measurement strategy allows organizations to track progress, quantify benefits, and make data-driven decisions. This section explores methods for evaluating cloud adoption success, monitoring and optimizing cloud performance, and establishing continuous improvement cycles.
Defining Success Metrics
Establishing clear and measurable success metrics is the first step in evaluating cloud adoption. These metrics should be aligned with the organization’s strategic goals and specific cloud adoption objectives. The choice of metrics will vary depending on the business context, but they generally fall into categories such as financial performance, operational efficiency, security posture, and business agility. Defining these metrics upfront enables a structured approach to track progress.
Monitoring and Optimizing Cloud Performance
Continuous monitoring and optimization are vital for ensuring optimal cloud performance and cost-effectiveness. This involves proactively tracking key performance indicators (KPIs), analyzing trends, and implementing corrective actions. Cloud providers offer a variety of tools and services for monitoring resource utilization, application performance, and security events. Regularly reviewing these metrics allows for identification of bottlenecks, inefficiencies, and potential security vulnerabilities. This proactive approach facilitates optimization.
Importance of Continuous Improvement and Feedback Loops
Continuous improvement is a core principle of successful cloud adoption. It involves establishing feedback loops to gather insights, identify areas for improvement, and iteratively refine cloud strategies and implementations. Feedback should be collected from various sources, including application performance data, user experiences, security audits, and cost analysis. These insights should then be used to drive ongoing improvements in areas such as resource allocation, application architecture, security configurations, and operational processes.
This continuous cycle ensures ongoing value.
Key Metrics for Evaluating Cloud Adoption Success
A comprehensive set of metrics is essential for a holistic evaluation of cloud adoption success. These metrics should be tracked regularly and analyzed to identify trends and inform decision-making. The following table provides a framework for evaluating cloud adoption success, categorized by key areas:
| Metric Category | Specific Metrics | Measurement Frequency | Example of Desired Outcome |
|---|---|---|---|
| Financial Performance |
| Monthly, Quarterly | Reduction in TCO by 15% within the first year. |
| Operational Efficiency |
| Weekly, Monthly | Increased deployment frequency from once a month to daily. MTTR reduced by 50%. |
| Security Posture |
| Weekly, Monthly | Reduction in the number of security incidents by 20%. Full compliance with industry regulations. |
| Business Agility |
| Monthly, Quarterly | Reduced time to market for new features by 30%. Scalability to handle a 2x increase in user traffic. |
For example, consider a retail company migrating its e-commerce platform to the cloud. They could track the following metrics:* Financial Performance: Track TCO to ensure cost savings compared to on-premises infrastructure. Monitor cloud spend against the allocated budget to maintain financial control.
Operational Efficiency
Measure deployment frequency to determine how quickly new features are released. Assess MTTR to evaluate the platform’s resilience and recovery capabilities.
Security Posture
Monitor the number of security incidents to ensure a secure environment. Track compliance with PCI DSS regulations.
Business Agility
Measure the time it takes to launch new promotions or campaigns. Track customer satisfaction to ensure a positive user experience.By consistently tracking these metrics and iterating on cloud strategies based on the results, organizations can drive continuous improvement and maximize the value of their cloud adoption initiatives.
Outcome Summary
In conclusion, mastering the AWS Cloud Adoption Framework (CAF) is not merely a technical exercise; it’s a strategic imperative for achieving digital transformation. By systematically addressing the Business, People, Governance, Platform, and Security perspectives, organizations can build a robust cloud foundation, drive innovation, and achieve measurable business outcomes. Continuous monitoring, iterative improvement, and a commitment to ongoing adaptation are crucial for long-term success.
Embracing the CAF allows organizations to unlock the full potential of the cloud, fostering agility, scalability, and a competitive edge in today’s dynamic business landscape.
Top FAQs
What is the primary benefit of using the AWS CAF?
The primary benefit is a structured, holistic approach to cloud adoption that aligns technology with business goals, mitigates risks, and accelerates value realization.
How long does it typically take to fully implement the AWS CAF?
The timeframe varies based on the organization’s size, complexity, and existing cloud maturity, ranging from several months to multiple years for full implementation and optimization.
What are the key challenges in implementing the CAF?
Key challenges include organizational change management, skills gaps, aligning business and IT objectives, and establishing robust governance policies.
How does the CAF help with cost optimization?
The Business Perspective of the CAF includes strategies for cost optimization, such as selecting the right services, right-sizing resources, and leveraging cost management tools.
Is the AWS CAF only for large enterprises?
No, the AWS CAF is adaptable and beneficial for organizations of all sizes, from startups to large enterprises, providing a scalable approach to cloud adoption.