Avoiding the Golden Hammer: Preventing Technology Overkill
The "golden hammer" anti-pattern, where developers over-rely on a single technology, can significantly impede project success by limiting innovation a...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

The "golden hammer" anti-pattern, where developers over-rely on a single technology, can significantly impede project success by limiting innovation a...
This article provides a thorough exploration of phishing attacks, outlining their deceptive tactics and potential impact on your digital security. Lea...

Safeguarding your cloud environment begins with a thorough vulnerability assessment. This guide provides a structured approach to identifying and miti...
Managing security across a multi-cloud environment requires a strategic approach to avoid fragmentation and ensure consistent protection. This guide o...
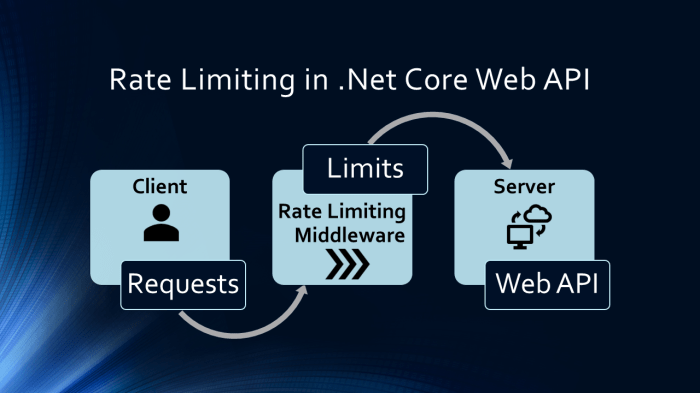
Serverless APIs, while offering scalability, are susceptible to resource exhaustion and denial-of-service attacks. This article explores the critical...
This comprehensive guide provides a detailed exploration of techniques to significantly reduce Docker image sizes, covering strategies from image buil...
Ensuring a smooth transition after a migration requires robust post-migration monitoring to identify and address potential issues. This article delves...
This comprehensive guide explores the critical aspects of infrastructure monitoring and alerting, providing a roadmap for building robust and proactiv...

Effectively communicating a migration plan to stakeholders is crucial for its success. This article provides a comprehensive guide to crafting a robus...

This article offers a practical roadmap for seamlessly integrating Artificial Intelligence (AI) services into your existing applications, unlocking en...

Cloud environments present unique challenges for security forensics, but understanding the core principles is crucial for effective investigation. Thi...

This comprehensive guide delves into the critical role of Cloud Workload Protection Platforms (CWPP) in modern cloud security, exploring its core conc...