
FinOps Adoption: Strategies for Securing Stakeholder Buy-In
Successfully implementing FinOps requires crucial stakeholder buy-in. This comprehensive guide outlines a strategic approach, from identifying key sta...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Successfully implementing FinOps requires crucial stakeholder buy-in. This comprehensive guide outlines a strategic approach, from identifying key sta...

This article explores the critical role of the circuit breaker pattern in building resilient microservices. Learn how circuit breakers safeguard your...
Considering the limitations and potential drawbacks of AWS Lambda, this article explores a comprehensive range of alternatives for serverless computin...

Navigating the complexities of chargebacks is crucial for any business accepting online payments. This comprehensive guide provides a detailed overvie...
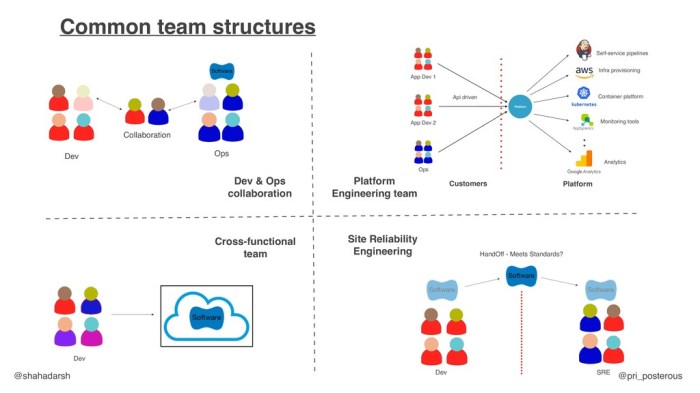
Platform engineering teams are vital in modern software development, providing the infrastructure and tools that streamline the entire development lif...

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...
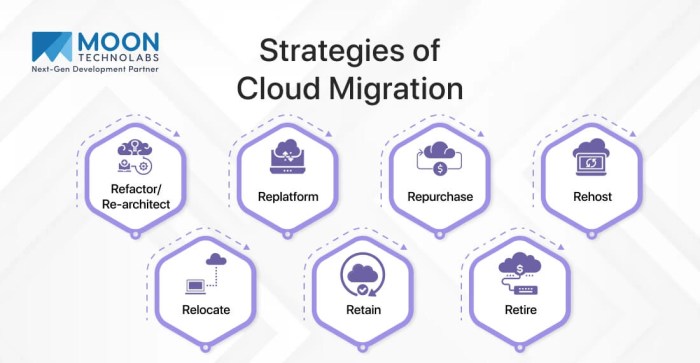
Navigating a cloud migration requires a robust DNS strategy to ensure seamless operation and optimized performance. This comprehensive guide delves in...

This article delves into the transformative impact of Artificial Intelligence (AI) and Machine Learning (ML) on cloud architecture, exploring their in...

Ensuring the reliability and maintainability of serverless applications hinges on effective unit testing of Lambda functions. This practice is crucial...
Discover insights and practical tips in this comprehensive guide about Guide To Serverless Error Handling And Retry Mechanisms.

Embarking on a cloud migration journey? This comprehensive guide provides a detailed checklist for enterprises, outlining the critical steps from init...

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...