
Cloud IAM Best Practices: Security, Compliance, and Efficiency
This comprehensive guide to Cloud Identity and Access Management (IAM) explores core concepts, best practices, and emerging trends to secure your clou...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide to Cloud Identity and Access Management (IAM) explores core concepts, best practices, and emerging trends to secure your clou...

Data classification is a fundamental practice in information security, involving the categorization of data based on its sensitivity and importance. T...

This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...
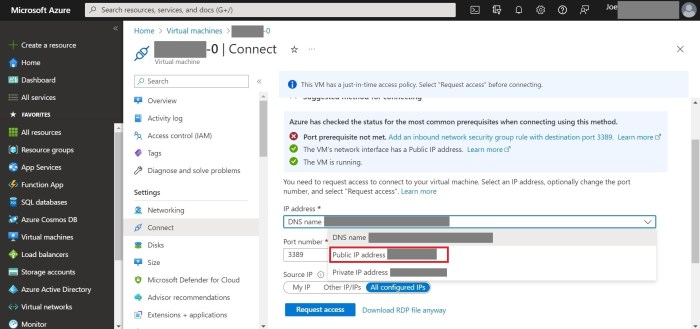
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...

Achieving FinOps success hinges on a comprehensive understanding and measurement of key metrics across cost optimization, resource utilization, financ...
Choosing between SQL and NoSQL databases is a critical decision for any application. This comprehensive guide provides a thorough comparison, analyzin...

This comprehensive guide provides a thorough introduction to Ansible, a powerful tool for automating configuration management. From setting up your en...

Data security is crucial for modern businesses, highlighting the need for effective backup and disaster recovery (BDR) strategies. This guide provides...

This article explores the crucial architectural patterns underpinning modern AI applications, covering essential designs like microservices, event-dri...

Effectively managing cloud spending is critical for businesses in today's digital environment. This article outlines the essential strategies for trac...
This comprehensive guide provides a deep dive into automating rollback procedures to mitigate the impact of failures in your deployments. From definin...

Ready to streamline your DevOps workflows? This article introduces Value Stream Mapping (VSM), a critical technique for visualizing and analyzing your...