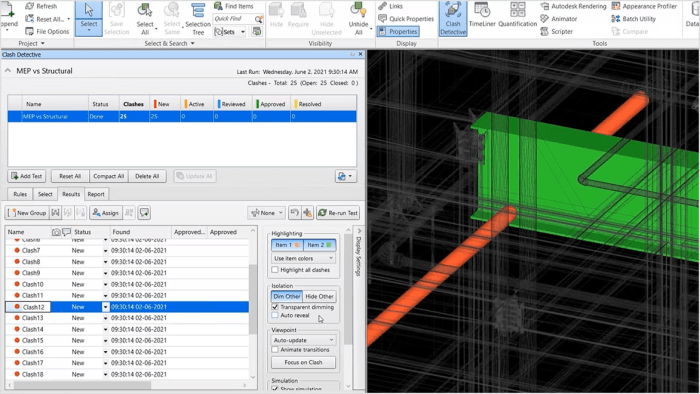
Cache Invalidation: Best Practices and Strategies
This article delves into the crucial practice of cache invalidation, a key element in optimizing web performance and user experience. Understanding an...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article delves into the crucial practice of cache invalidation, a key element in optimizing web performance and user experience. Understanding an...

This article explores the critical "Don't Repeat Yourself" (DRY) principle in software development, a cornerstone for writing efficient and maintainab...
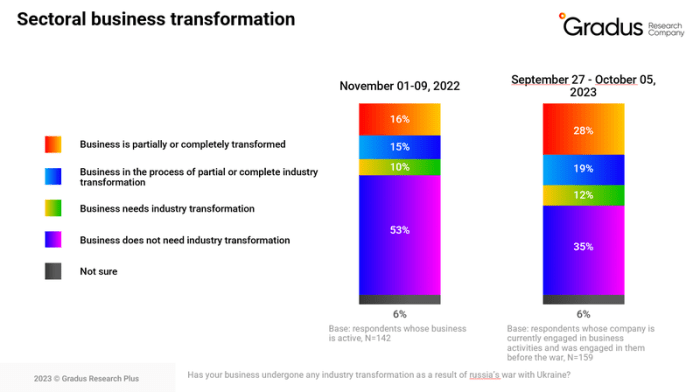
Technology migration projects are complex, but learning from the successes and failures of other companies can significantly improve your own outcomes...

Application portfolio analysis is a vital, yet often overlooked, step in digital transformation, providing a data-driven understanding of an organizat...

Privacy-preserving computation offers a groundbreaking approach to data security, enabling the processing of encrypted data without the need for decry...

This comprehensive guide provides a crucial roadmap for securing Infrastructure as Code (IaC) templates, addressing the inherent security challenges o...

This article provides a comprehensive cost-benefit analysis of serverless query processing, examining its core concepts, advantages, and real-world ap...
This comprehensive guide provides a step-by-step approach to designing a robust cloud storage backup strategy, covering crucial aspects from defining...

This article provides a comprehensive overview of Amazon Aurora Serverless, exploring its core concepts, architecture, and benefits for database manag...

This comprehensive guide explores the ISO 27001 standard, a globally recognized framework for information security management. From its core principl...
Containerization and Kubernetes offer a significant advancement in application deployment, driven by the need for improved efficiency and flexibility....
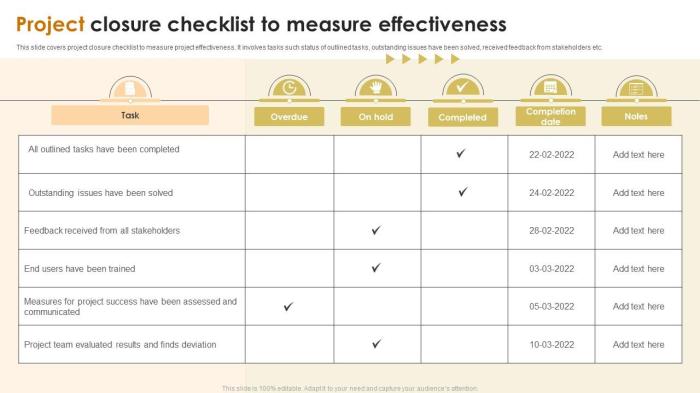
In today's evolving threat landscape, measuring the effectiveness of your security program is paramount. This guide provides a structured approach to...