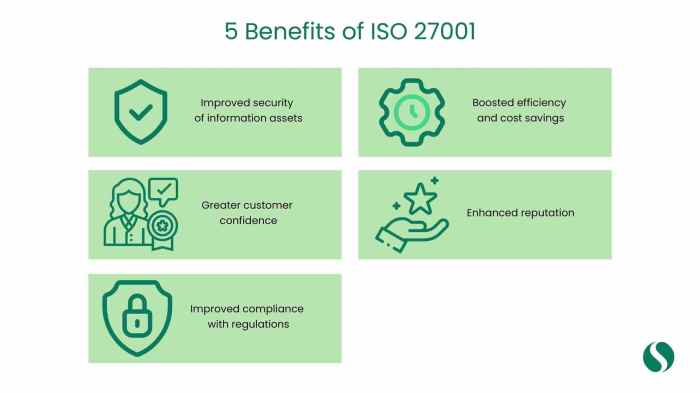
ISO 27001 Certification: A Step-by-Step Guide
This comprehensive guide provides a detailed roadmap for achieving ISO 27001 certification, covering everything from understanding the core principles...
152 posts in this category

This comprehensive guide provides a detailed roadmap for achieving ISO 27001 certification, covering everything from understanding the core principles...
Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...
"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...

This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...

Protect your organization from the potential pitfalls of cloud service provider failures with a robust third-party vendor risk assessment program. Thi...

This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...

This article explores the pivotal role of service meshes in securing modern, microservices-based application architectures. It highlights how service...
This article offers a comprehensive guide to negotiating robust security provisions within your cloud service level agreement (SLA). It covers critica...

Data classification is a fundamental practice in information security, involving the categorization of data based on its sensitivity and importance. T...
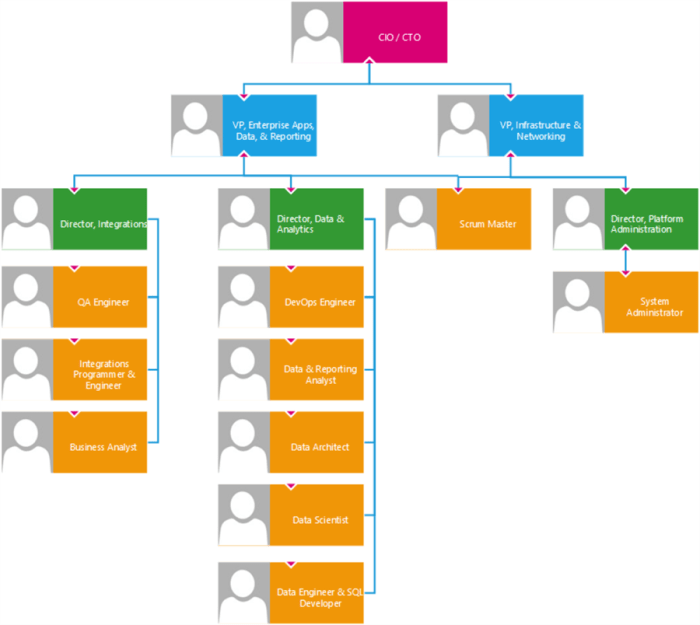
Cloud computing's scalability demands stringent security measures, making clear role and responsibility definitions for cloud access paramount. This a...

This comprehensive guide provides a detailed overview of FedRAMP, the critical security authorization program for cloud services used by the U.S. gove...

This comprehensive guide details the essential skills required to excel as a Cloud Security Engineer, covering core technical competencies like networ...