
Building Threat Hunting Capabilities: A Practical Guide
This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...
152 posts in this category

This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...
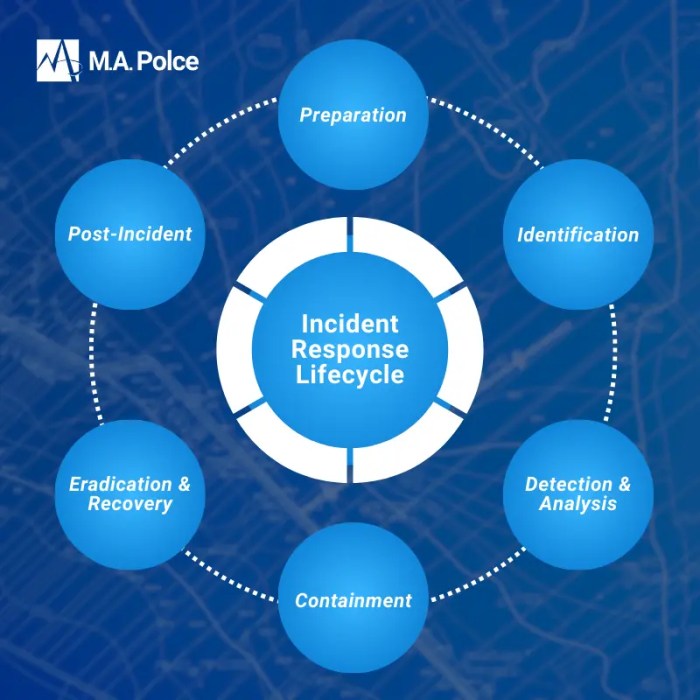
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...
This comprehensive guide delves into the critical aspects of secure logging and monitoring within cloud environments, exploring its fundamental concep...
In today's cloud-centric world, understanding Data Loss Prevention (DLP) solutions is critical for safeguarding sensitive information. This article pr...

Privacy-preserving computation offers a groundbreaking approach to data security, enabling the processing of encrypted data without the need for decry...

In the ever-evolving cloud environment, safeguarding your digital assets is critical, and Cloud Infrastructure Entitlement Management (CIEM) tools off...
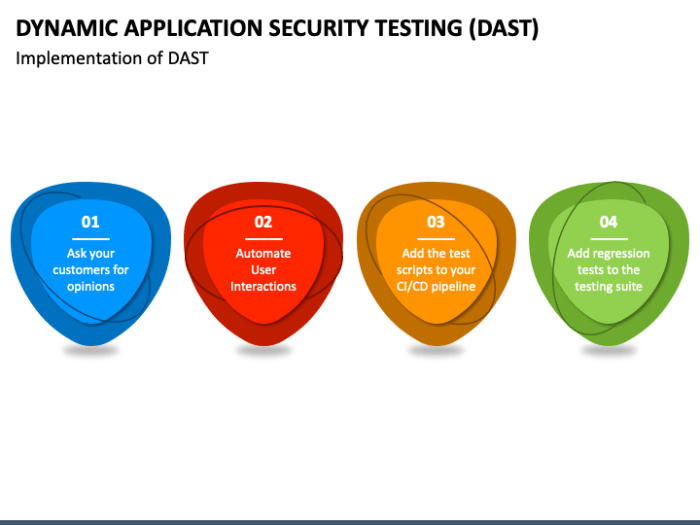
This comprehensive guide explores Dynamic Application Security Testing (DAST), providing a deep dive into its core concepts, functionality, and practi...

This article provides a comprehensive overview of Software Bill of Materials (SBOMs), explaining their definition, purpose, and benefits for various s...

Effectively securing your cloud infrastructure requires a deep understanding of both Security Groups and Network ACLs. This comprehensive guide delves...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...

This comprehensive guide explores the critical importance of securing your software dependencies, outlining potential risks from supply chain attacks...