
Cloud Access Security Broker (CASB): Definition, Benefits, and How It Works
This article provides a comprehensive overview of Cloud Access Security Brokers (CASBs), outlining their core functions, architecture, and key feature...
152 posts in this category

This article provides a comprehensive overview of Cloud Access Security Brokers (CASBs), outlining their core functions, architecture, and key feature...

Navigating HIPAA compliance in the cloud requires a strategic approach that addresses data security, access controls, and disaster recovery. This comp...
Protecting sensitive information is paramount in today's data-driven world, and this comprehensive guide provides a deep dive into implementing effect...

The digital world is constantly evolving, and staying informed about the latest security threats and vulnerabilities is crucial for both individuals a...
Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...

In the modern cloud-centric business environment, robust data and infrastructure security is critical. Security Information and Event Management (SIEM...
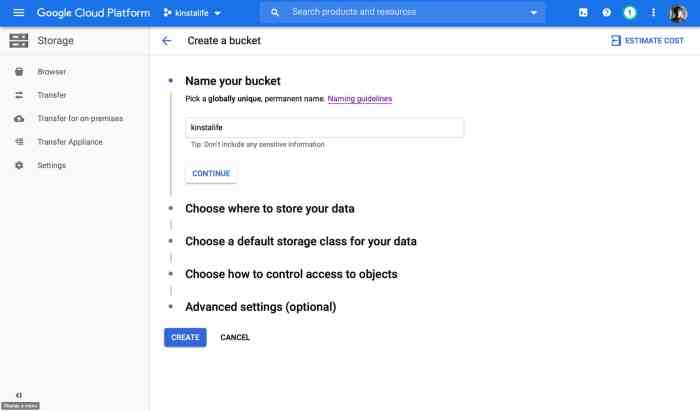
With the increasing reliance on cloud storage, securing your buckets from misconfiguration is crucial. This article delves into the unique security ch...
This article provides a thorough exploration of phishing attacks, outlining their deceptive tactics and potential impact on your digital security. Lea...

This article provides a comprehensive guide to Tactics, Techniques, and Procedures (TTPs), crucial elements for understanding and combating cyber thre...
This comprehensive article delves into the transformative technology of homomorphic encryption, exploring its core functionality, diverse types, and u...
Want to strengthen your organization's digital defenses? This guide offers a comprehensive approach to conducting a security architecture review, prov...

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...