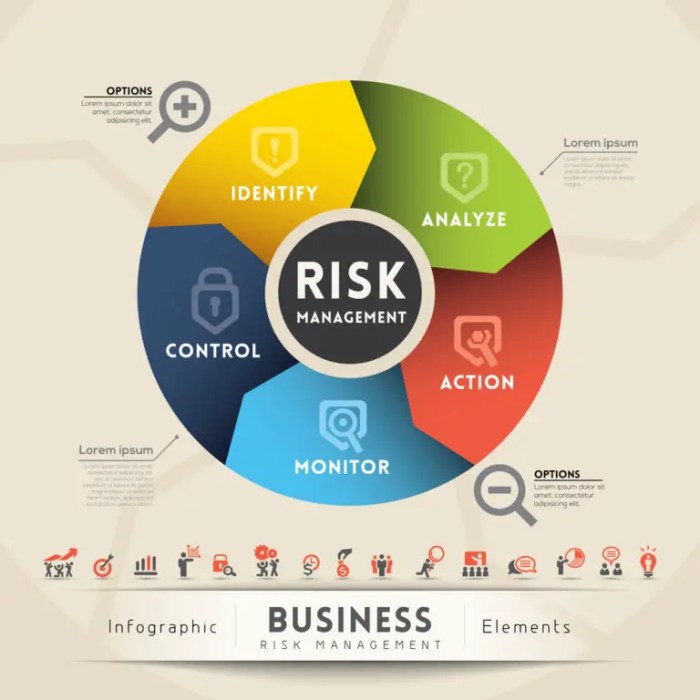
Key Risk Indicators (KRIs) for Cybersecurity: A Comprehensive Guide
Cybersecurity Key Risk Indicators (KRIs) serve as vital early warning signals, enabling organizations to proactively manage and mitigate evolving cybe...
152 posts in this category

Cybersecurity Key Risk Indicators (KRIs) serve as vital early warning signals, enabling organizations to proactively manage and mitigate evolving cybe...
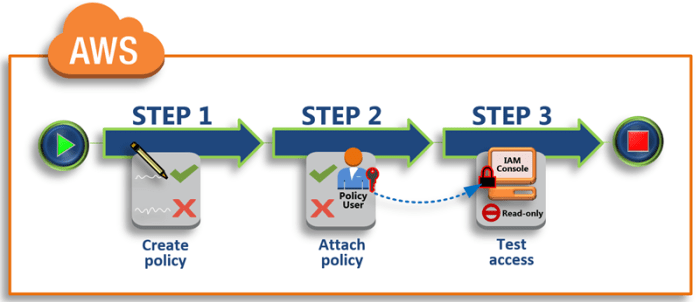
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...

In today's evolving digital landscape, cloud security certifications are crucial for professionals seeking to validate their expertise and advance the...

This article delves into the intricacies of legal hold and eDiscovery, focusing on the significant advantages of leveraging cloud technology for these...

In today's digital world, the Chief Information Security Officer (CISO) is a vital strategic leader, tasked with protecting an organization's data and...

Handling Data Subject Access Requests (DSARs) is a critical component of GDPR compliance. This comprehensive guide offers a clear and detailed roadmap...
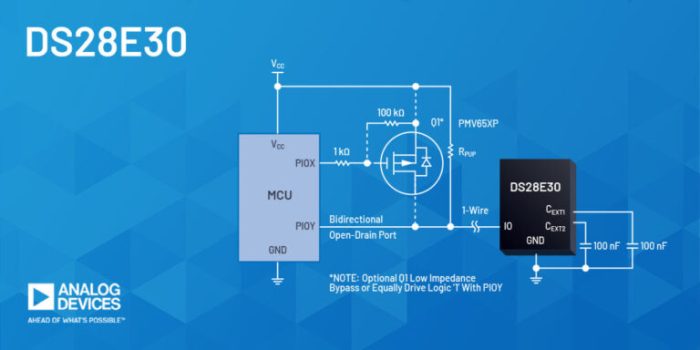
Protecting sensitive data in the cloud requires robust security measures, and this guide provides a comprehensive overview of data encryption. It delv...

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...
This article provides a comprehensive guide to implementing a Zero Trust security model within cloud environments, covering key principles, asset iden...

Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...

In the digital age, the integrity and admissibility of digital evidence are paramount for successful investigations. This article delves into the cruc...