
Secure Backup and Disaster Recovery: Strategies for Business Resilience
Data security is crucial for modern businesses, highlighting the need for effective backup and disaster recovery (BDR) strategies. This guide provides...
152 posts in this category

Data security is crucial for modern businesses, highlighting the need for effective backup and disaster recovery (BDR) strategies. This guide provides...

This article provides a comprehensive overview of User and Entity Behavior Analytics (UEBA), exploring its core concepts, components, and practical ap...
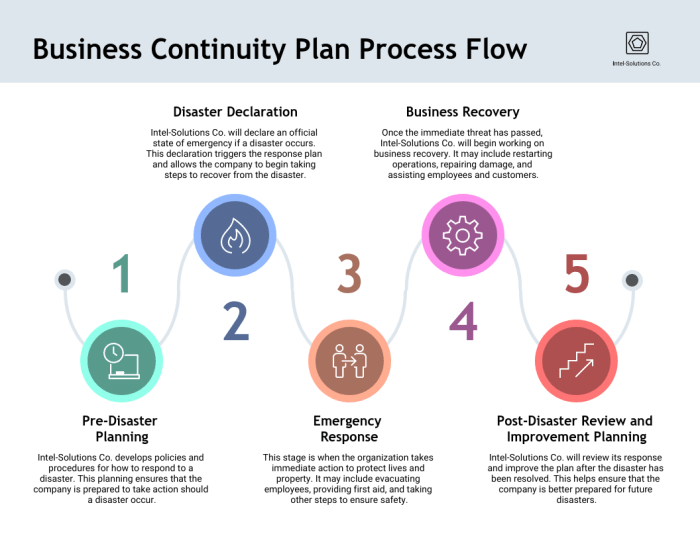
This comprehensive guide explores the essential integration of Business Continuity Planning (BCP) and Disaster Recovery (DR), providing a roadmap to e...

Effectively communicating cybersecurity risks to the board of directors is crucial for informed decision-making. This guide offers a comprehensive app...

Enhance your cybersecurity strategy by learning how to set up a honeypot, a valuable tool designed to attract and analyze potential attackers. This gu...

Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Breach Notifications.
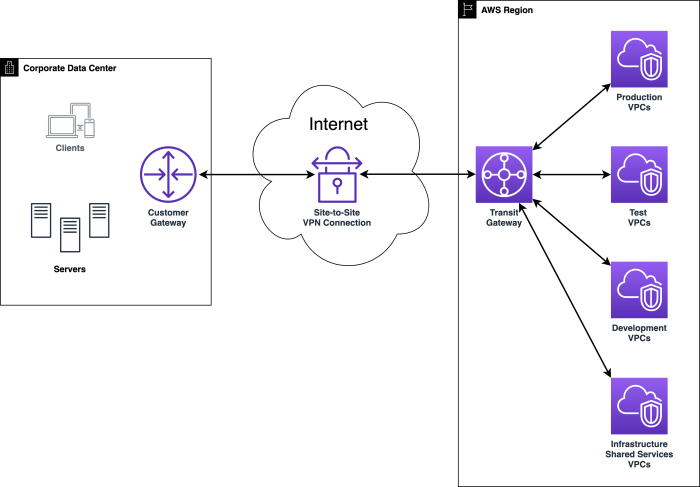
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...

This comprehensive guide delves into the MITRE ATT&CK framework, providing a roadmap for understanding its structure and leveraging its capabilities t...
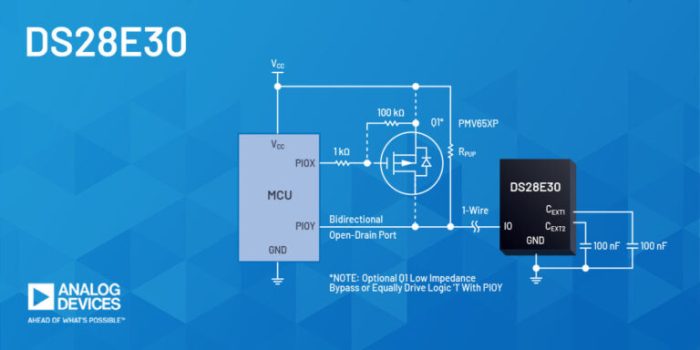
The proliferation of Internet of Things (IoT) devices necessitates robust security measures to protect against increasingly sophisticated cyber threat...
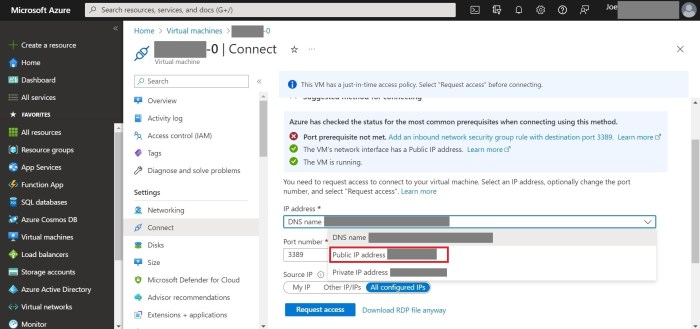
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...

This comprehensive article delves into Runtime Application Self-Protection (RASP), exploring its fundamental concepts, architecture, and operational m...
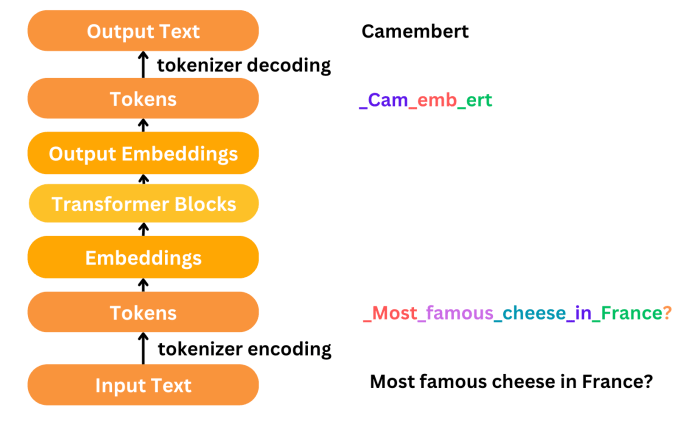
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...