
Cloud Secrets & Encryption Key Management: Best Practices & Tools
This article provides a comprehensive guide to managing secrets and encryption keys in the cloud, a critical aspect of cloud security. It explores fun...
152 posts in this category

This article provides a comprehensive guide to managing secrets and encryption keys in the cloud, a critical aspect of cloud security. It explores fun...
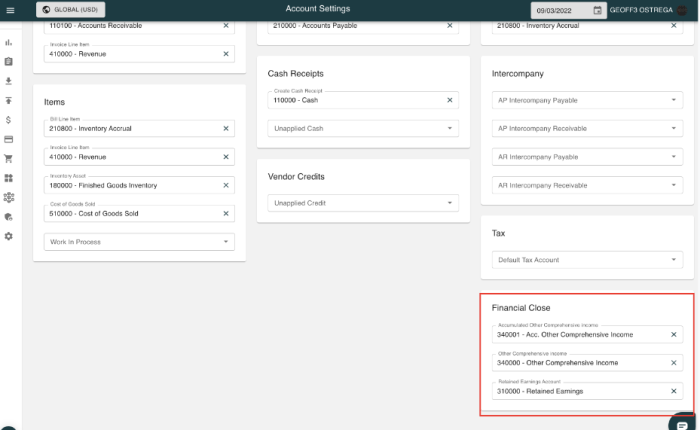
Configuration drift in security settings poses a significant threat, potentially weakening your defenses through unnoticed changes. Proactively monito...
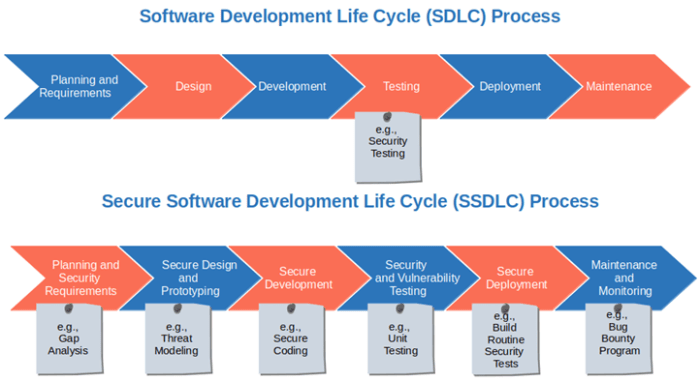
Protecting your software from vulnerabilities is paramount in today's digital world, and this guide provides a comprehensive approach to implementing...

This comprehensive guide explores the multifaceted landscape of container security, outlining critical best practices to protect your deployments from...

This article provides a comprehensive overview of Static Application Security Testing (SAST), exploring its core principles, role within the Software...

This comprehensive article delves into the emerging field of Confidential Computing, defining its core concepts, key technologies, and significant ben...

In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...

Navigate the complex legal landscape of cloud computing with this comprehensive guide. This article delves into critical areas like data privacy regul...
The increasing convergence of Internet of Things (IoT) devices and cloud services necessitates a thorough examination of the associated security risks...

The cloud offers significant advantages, but it also presents new vulnerabilities to malware and ransomware attacks. This article outlines essential s...
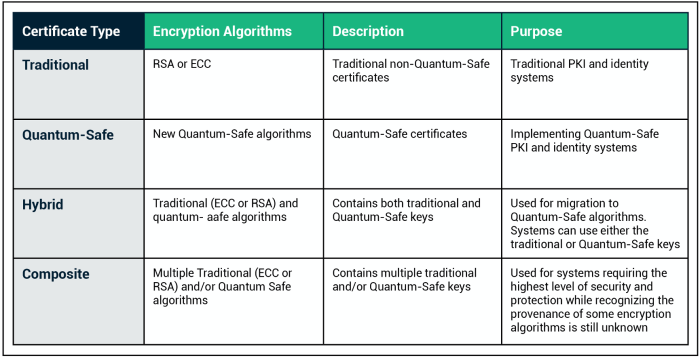
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...

This article delves into the intricacies of identity federation, explaining its core concepts, components, and the benefits it offers for streamlined...