
Breaking Into Cloud Security: A Beginner's Guide
This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...
152 posts in this category

This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...
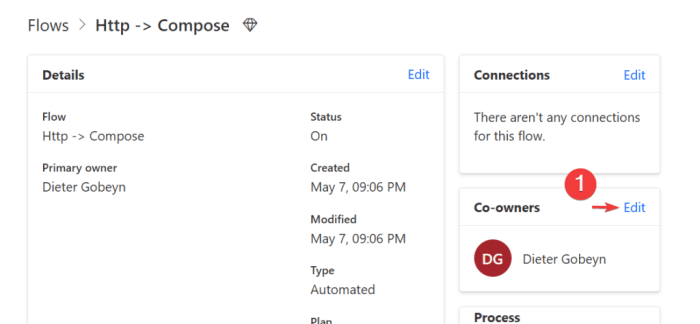
In today's dynamic digital environment, automating security policy enforcement is paramount. This guide provides a comprehensive overview, covering es...

In today's complex regulatory environment, establishing a robust data retention policy is crucial for compliance and minimizing potential risks. This...

Safeguarding a data lake environment requires a multi-faceted approach. This article provides a comprehensive guide to securing your data lake, coveri...

Safeguarding your digital assets requires vigilant monitoring for unauthorized file changes. This article explores the critical importance of detectin...
In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...
User Lifecycle Management (ULM) and provisioning are crucial for security, operational efficiency, and compliance within any organization. This guide...
Managing resources across multiple cloud providers like AWS, Azure, and GCP introduces complex challenges for consistent security and access control d...
Protecting sensitive data in the digital age demands robust security measures. This guide provides a detailed overview of enforcing strong authenticat...
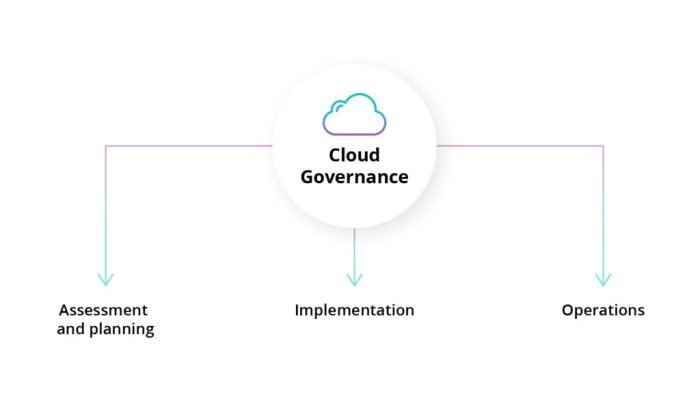
Establishing a formal cloud security governance framework is crucial for protecting valuable assets and maintaining compliance in the cloud. This fram...
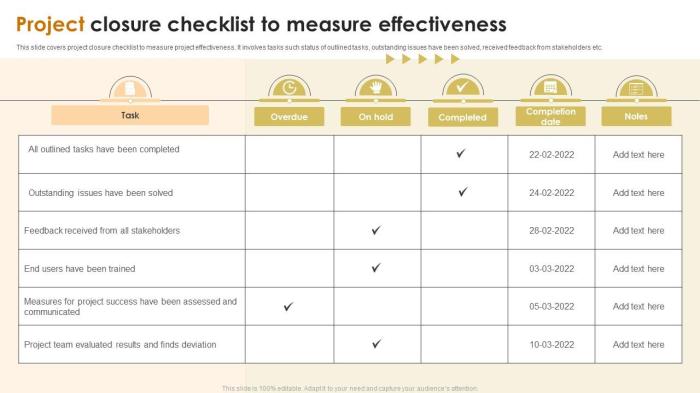
In today's evolving threat landscape, measuring the effectiveness of your security program is paramount. This guide provides a structured approach to...

This article provides a comprehensive overview of Data Privacy Impact Assessments (DPIAs), essential tools for protecting personal information in the...