
Kubernetes Secrets Management: Best Practices and Strategies
Protecting sensitive data within Kubernetes is crucial for the security of your deployments. This article provides a comprehensive guide to managing s...
167 posts in this category

Protecting sensitive data within Kubernetes is crucial for the security of your deployments. This article provides a comprehensive guide to managing s...

Feature flags are a powerful technique for modern software development, offering a way to control the release, testing, and deployment of features. Th...

This comprehensive guide delves into the critical practice of container vulnerability scanning, explaining its core concepts and importance in securin...

Load balancing is a critical component of modern network infrastructure, designed to optimize performance and reliability by distributing traffic acro...
This comprehensive guide provides a deep dive into automating rollback procedures to mitigate the impact of failures in your deployments. From definin...

This article delves into the crucial role of the health check API endpoint in software development, explaining its function as a vital monitoring tool...

Discover the Saga pattern, a vital strategy for ensuring data consistency within distributed transactions in microservices architectures. This article...
This article provides a comprehensive overview of Chaos Engineering within a DevOps context, detailing its principles, goals, and practical implementa...

This comprehensive guide explores the power of Redis for both caching and session storage, detailing its core functionalities, data structures, and ad...

This guide provides a comprehensive roadmap for organizations seeking to adopt a DevOps culture, emphasizing streamlined processes, improved collabora...
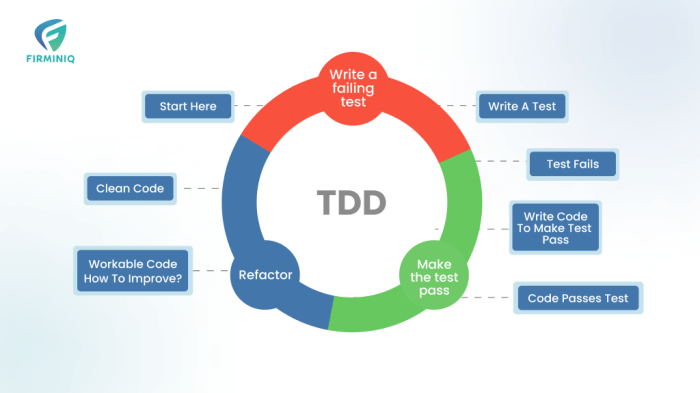
Test-Driven Development (TDD) is a software development methodology that prioritizes testing *before* code creation, a reversal of the traditional pro...

Managing microservices communication presents intricate challenges, but Istio offers a comprehensive solution. This guide explores Istio's capabilitie...