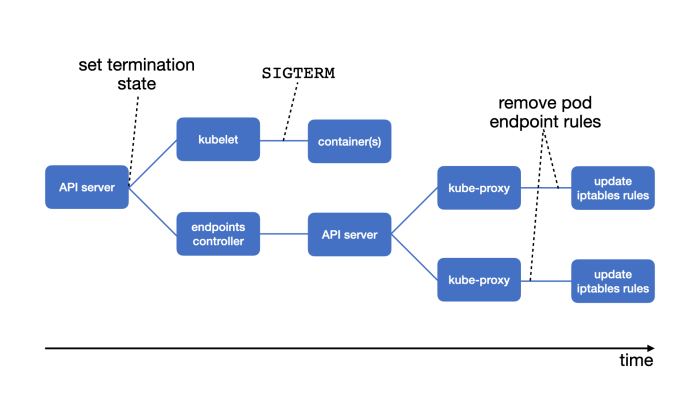
Kubernetes Network Policies: Securing Your Clusters with Fine-Grained Control
Kubernetes Network Policies act as cloud-native firewalls, providing essential security for containerized applications within your clusters. This arti...
167 posts in this category

Kubernetes Network Policies act as cloud-native firewalls, providing essential security for containerized applications within your clusters. This arti...
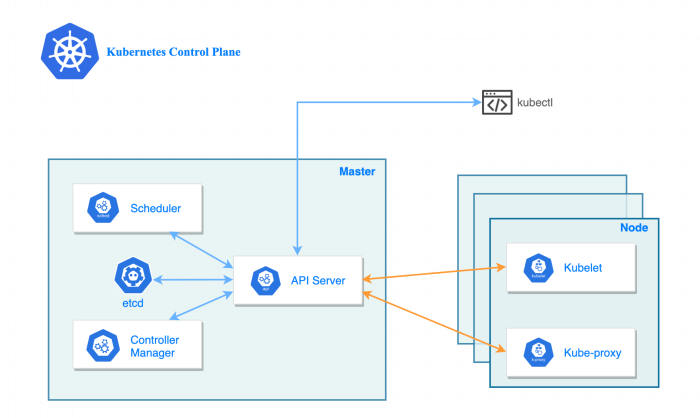
Kubernetes (K8s) is a transformative orchestration platform designed to revolutionize application deployment and management in today's dynamic digital...

Securing your Infrastructure as Code (IaC) templates is paramount for mitigating risks associated with automated deployments. This guide provides esse...
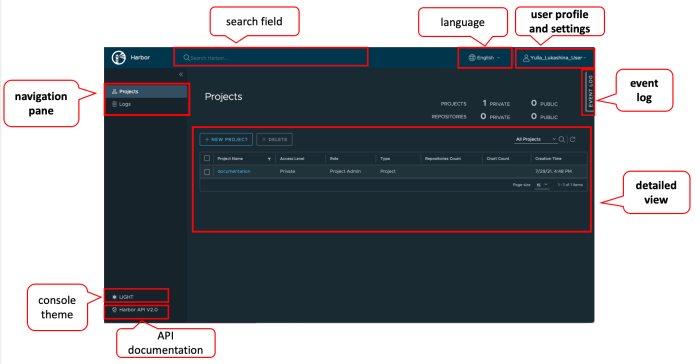
In the dynamic world of software development, container registries play a crucial, yet often overlooked, role. Serving as a secure and organized repos...
This comprehensive guide provides a detailed exploration of techniques to significantly reduce Docker image sizes, covering strategies from image buil...

To maintain application health and optimize resource utilization within your Kubernetes clusters, robust monitoring is essential. This comprehensive g...

This article provides a comprehensive guide to containerizing your Java applications with Docker, enabling enhanced agility, scalability, and deployme...

Cloud Development Kits (CDKs) are transforming cloud infrastructure management by enabling developers to define their cloud setups using familiar prog...
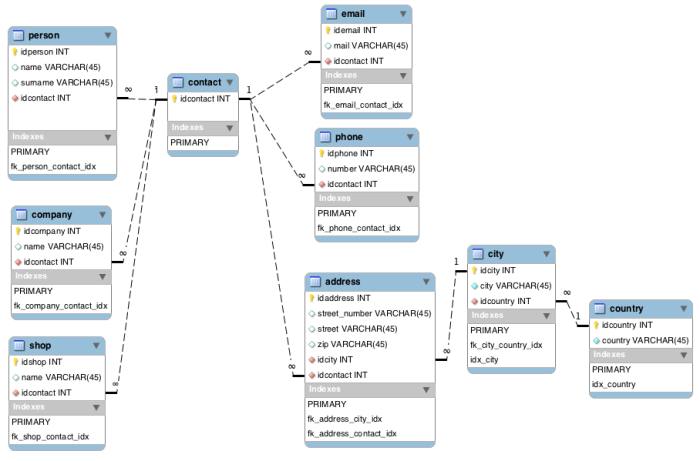
The Database-per-Service pattern is a key architectural consideration when implementing microservices, advocating for each service to possess its own...
This comprehensive article explores the critical role of artifact management in DevOps, providing a deep dive into its core concepts and practical app...

This comprehensive guide provides a step-by-step approach to implementing GitOps with Argo CD, covering everything from foundational principles to adv...

Minimize disruptions and maximize success by understanding and reducing your change failure rate. This comprehensive guide delves into identifying roo...